Entra ID: External Authentication Methods
Please note, this integration is in a beta phase. Please provide any feedback or enhancement requests to your HYPR Account Manager and these will be worked into our next release.
Microsoft Entra ID External Authentication Methods (EAM) has been launched as public preview in May 2024.
Integrating HYPR with Entra ID via External Authentication Methods (EAM) lets you access your organization's Entra ID-based applications (such as Office 365) using HYPR passwordless authentication as a phishing resistant multi-factor authentication method.
HYPR is part of the initial group of identity and authentication vendors supported by Entra as External Authentication Method providers. Learn more about the launch in the EAM public preview announcement and the HYPR announcement.
Getting the HYPR Entra ID External Authentication Methods (EAM) integration up and running requires the following basic steps:
-
Understand how the Entra ID login process changes for end users after you integrate with HYPR. See What Will Happen in Entra?.
-
Configure the Entra ID side of the integration. See Setting Up Entra ID.
-
Configure the HYPR side of the integration. See Connecting Entra to HYPR.
The following HYPR Integration common tasks are explained on the Integrations main page.
-
Choose the methods you want people to be able to use for passwordless authentication; see Allowing the Use of FIDO2 Authenticators
-
Monitor integration-specific user activity with the Audit Trail
Microsoft Entra ID External Authentication Methods (EAM) requires at least a Microsoft Entra ID P1 subscription. Please check your Microsoft subscription before proceeding with configuring the integration.
What Will Happen in Entra ID?
Login Flow
Once you activate the HYPR Entra ID EAM integration, users will experience a different Entra ID login flow.
Enrolled Users
Users who have been successfully enrolled via the HYPR Device Manager can fullfill multi-factor authentication requirements through HYPR. After providing their username on the Entra ID sign in screen and authenticating with their password, they'll be redirected to the HYPR passwordless authorization flow. Then they can use their registered HYPR authenticator to complete the login process and get back to Entra ID.
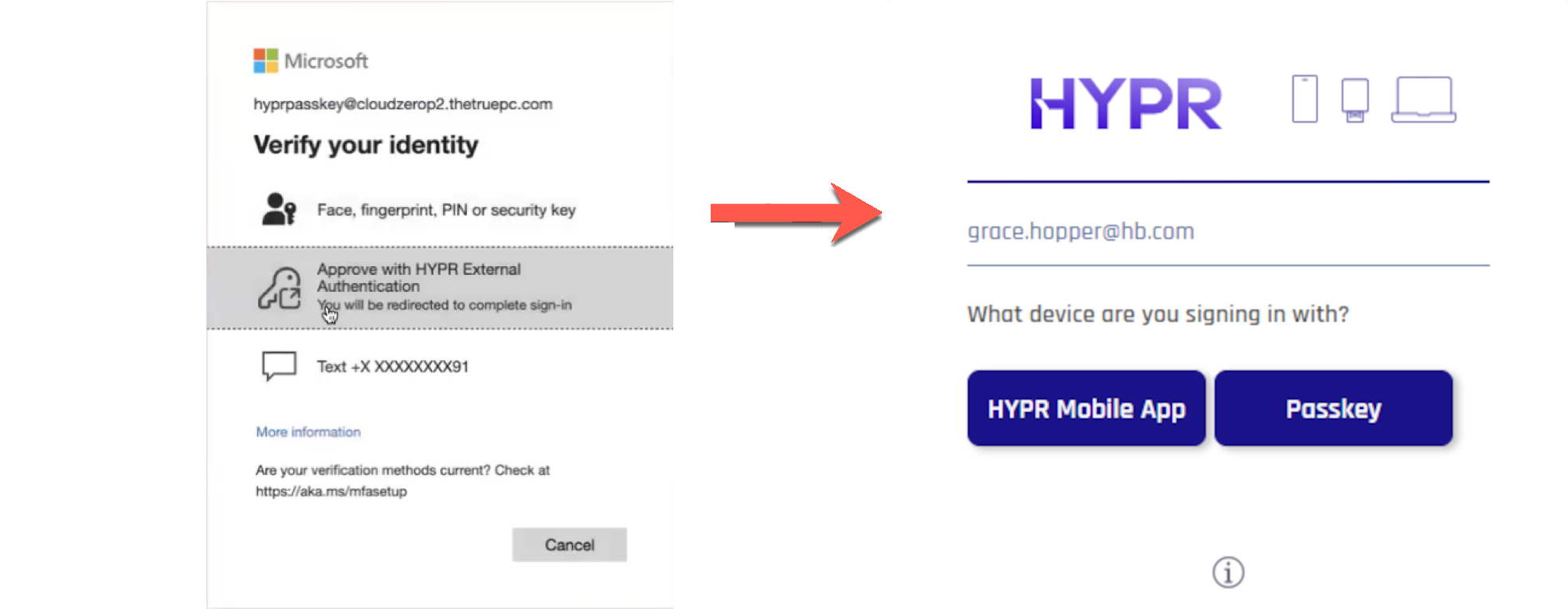
Behind the Scenes
Once you create the integration, HYPR will handle as much of the back-end configuration in Entra ID as possible.
Non-enrolled Group Membership
Users who haven't registered a device with HYPR before you activate the HYPR Entra ID EAM integration will automatically be added to a "Users Not Yet Enrolled" Entra ID group created by HYPR during the setup process. They'll automatically be removed from the non-enrolled group as soon as they register a device.
What You'll Need
-
Since you're setting up the HYPR Entra ID EAM integration through the HYPR Control Center, you should have already registered for an account, paired your mobile device with HYPR, and used your new passwordless login to access the Control Center; if this isn't the case, please contact HYPR Support and we'll help you out
-
Make sure you have the Entra tenant available and an account that exists on the
\*.onmicrosoft.comdomain with administrative privileges. -
Make sure you have the Entra licenses (P1) assigned to the test accounts
Setting Up Entra ID
Registering the HYPR Entra ID Application
-
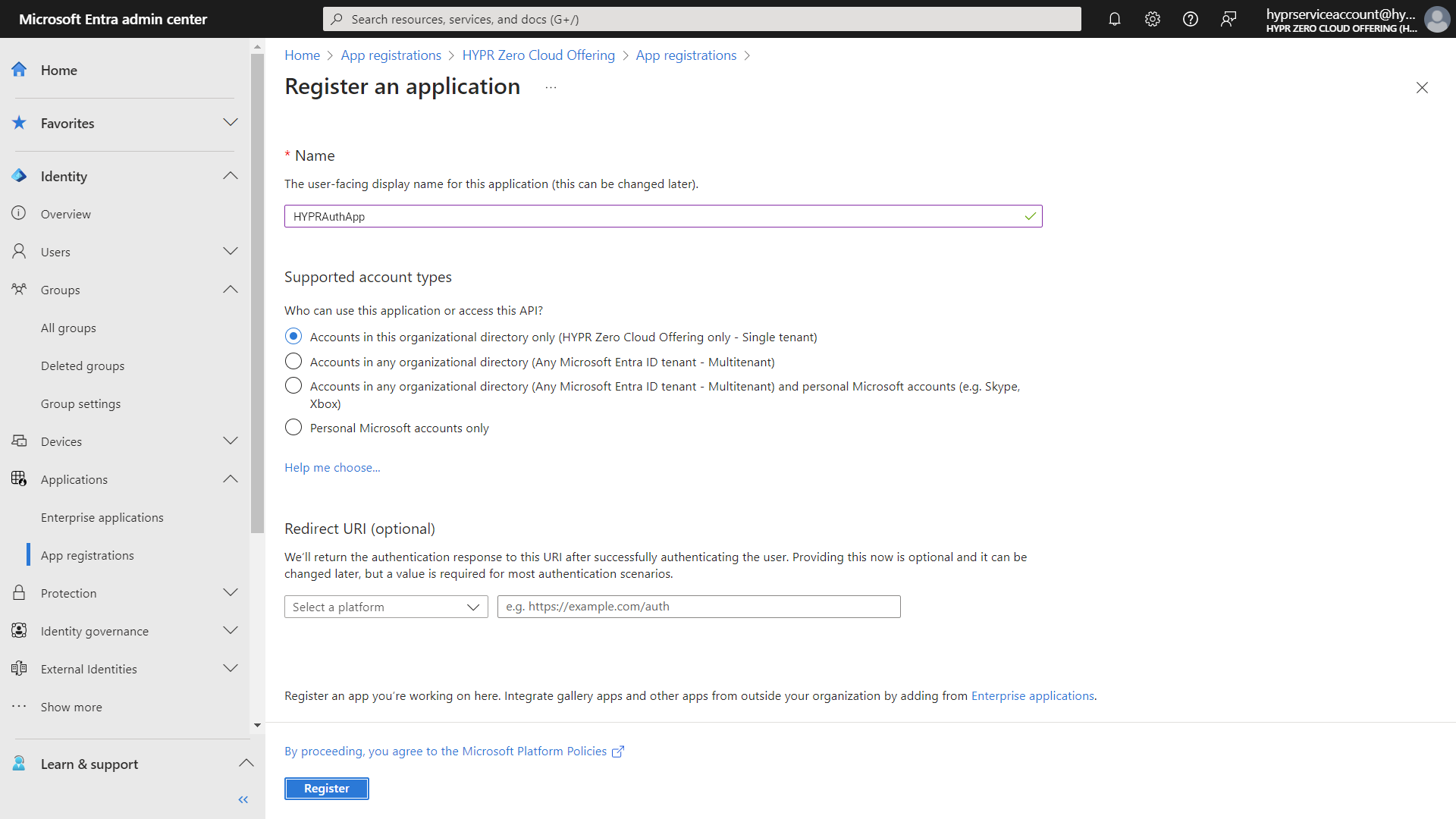
From the Entra ID portal home screen, select Entra ID > App registrations > New registration.
-
Enter the application name HYPRAuthApp and select Accounts in this organizational directory only.
-
Click Register when done.
-
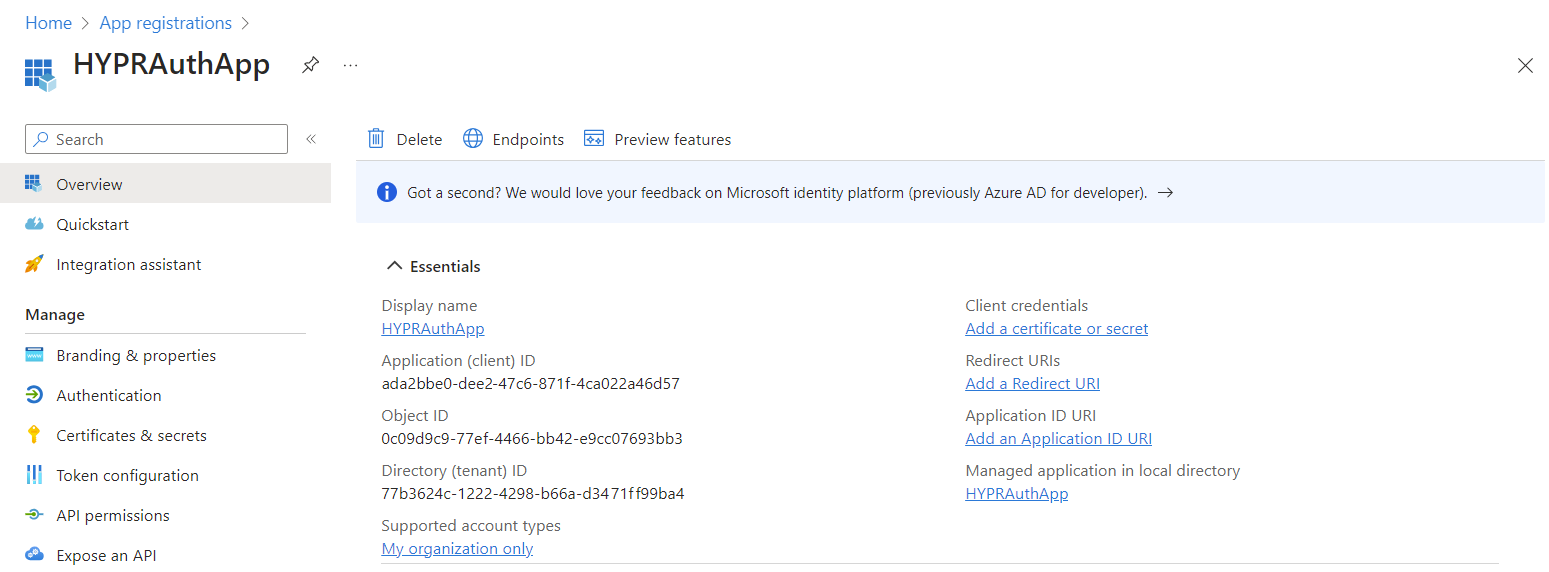
On the Overview page, make a note of the following values which you'll need later when configuring the integration in the HYPR Control Center:
-
Application (client) ID
-
Directory (tenant) ID
-
Granting Required API Permissions
-
From the Entra ID screen, select App registrations and select the app you just made.
-
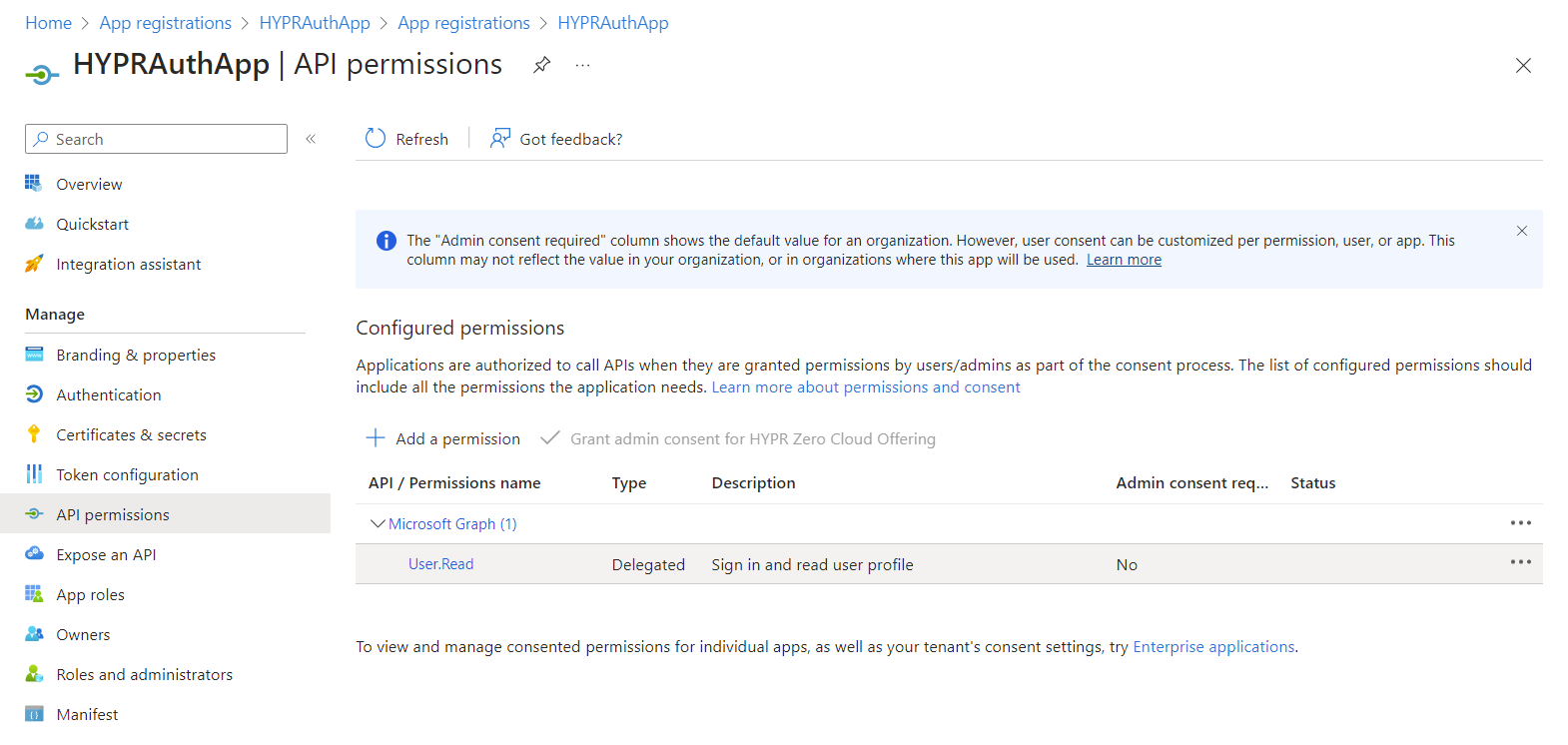
Select API permissions.
-
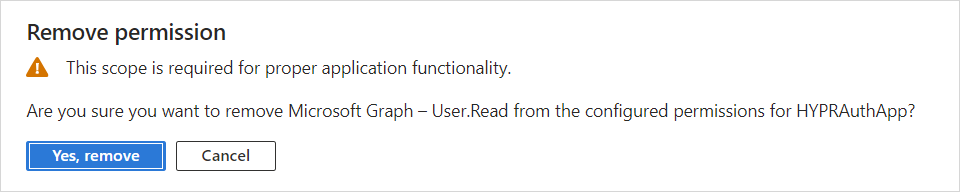
By default, the application will already have Microsoft Graph's User.Read permission. This isn't required, so remove it by clicking the ... icon and choosing Remove permission. Click Yes, remove to confirm when prompted.
-
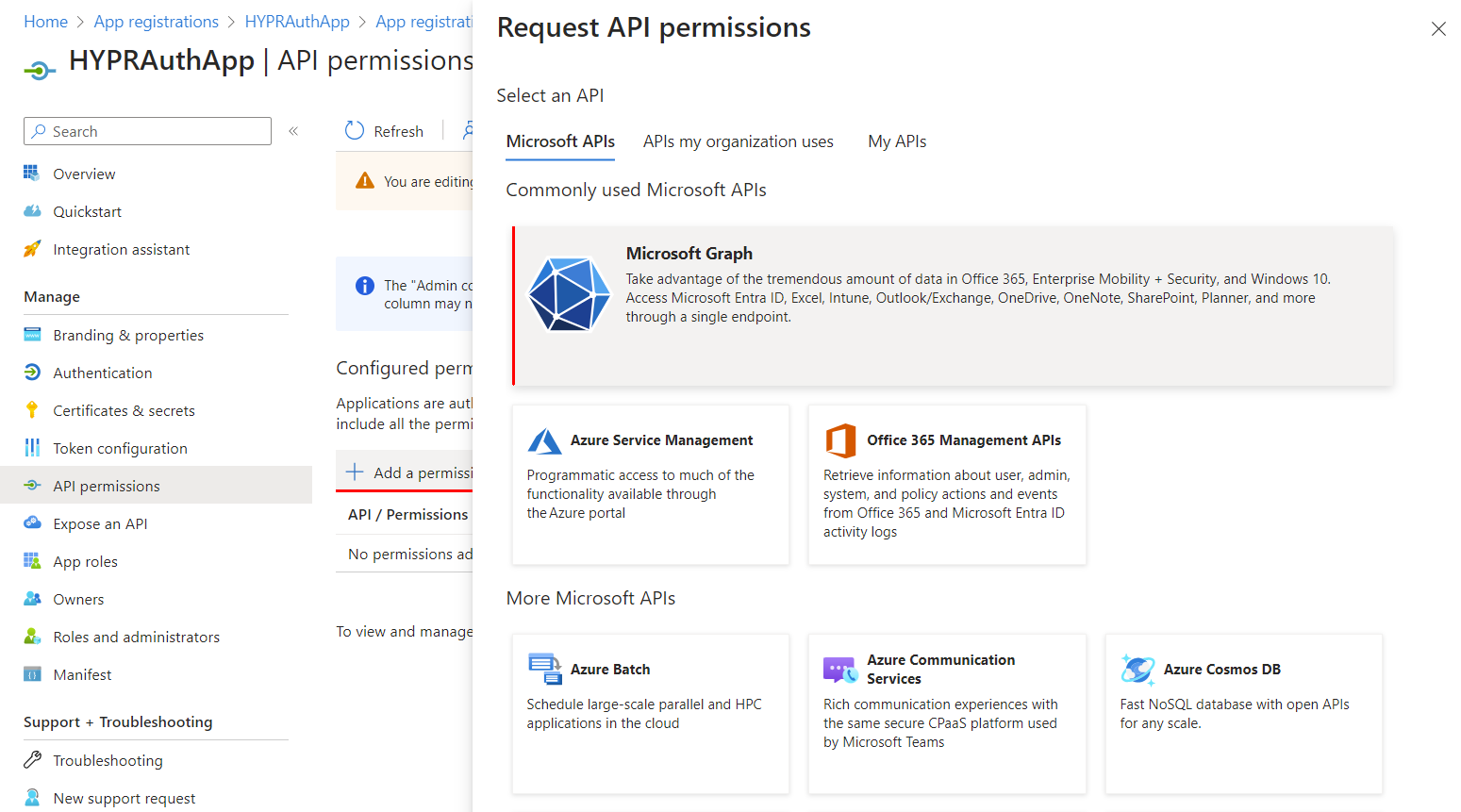
Click Add a permission, and on the tiled choices, select Microsoft Graph.
-
Select Delegated permissions.
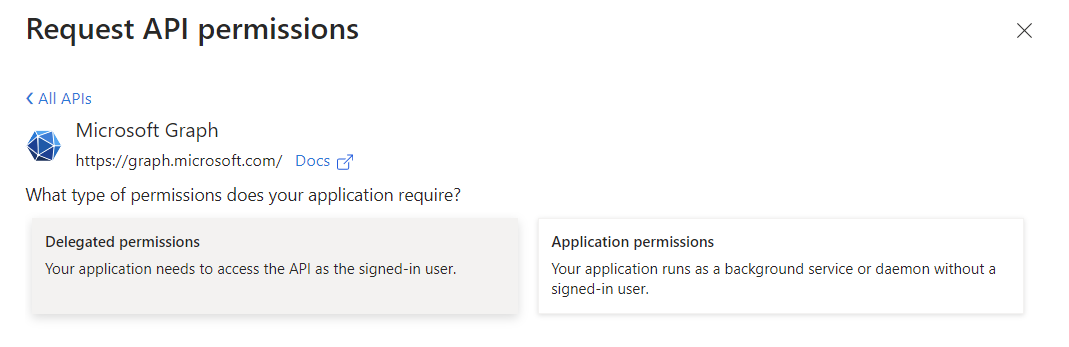
Delegated by DefaultSometimes Entra ID will not display the option for Delegated or Application permissions, and will immediately assume Delegated as the choice. After you grant Admin Consent later in the process, you will be able to verify the permission type.
-
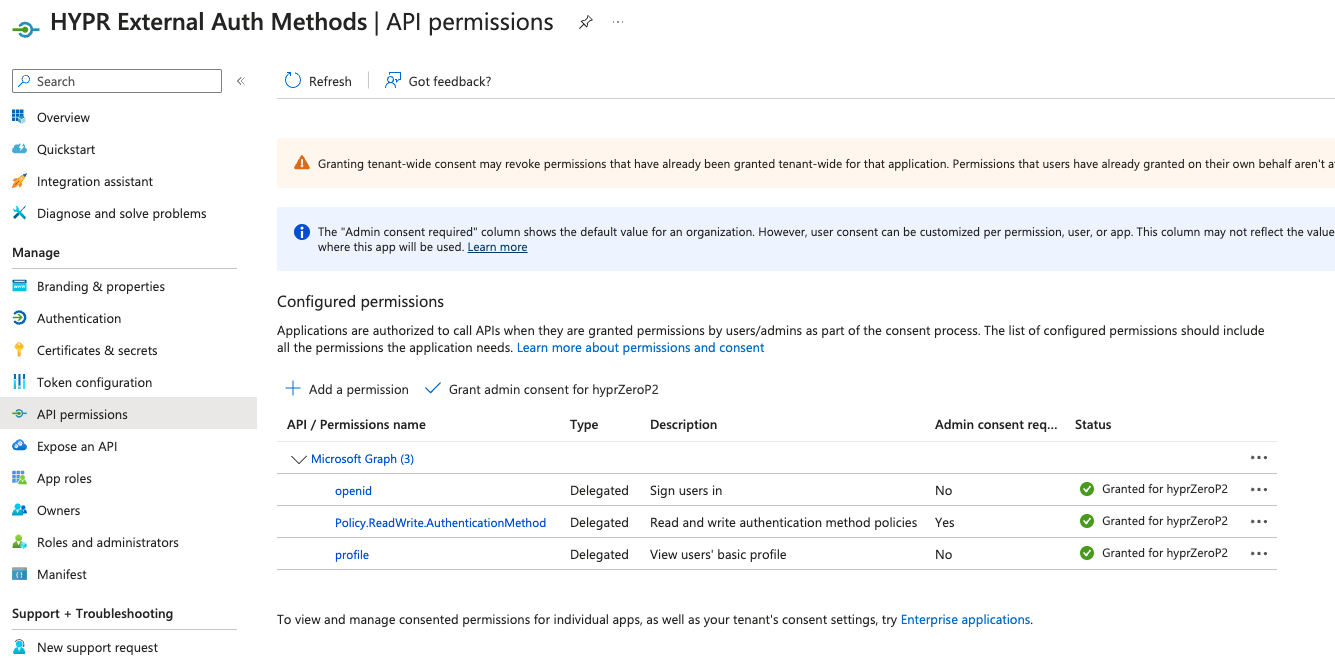
Locate and select the following:
-
openid -
Policy.ReadWrite.AuthenticationMethod -
profile
The API Permissions page now displays the new Delegated permissions.
-
-
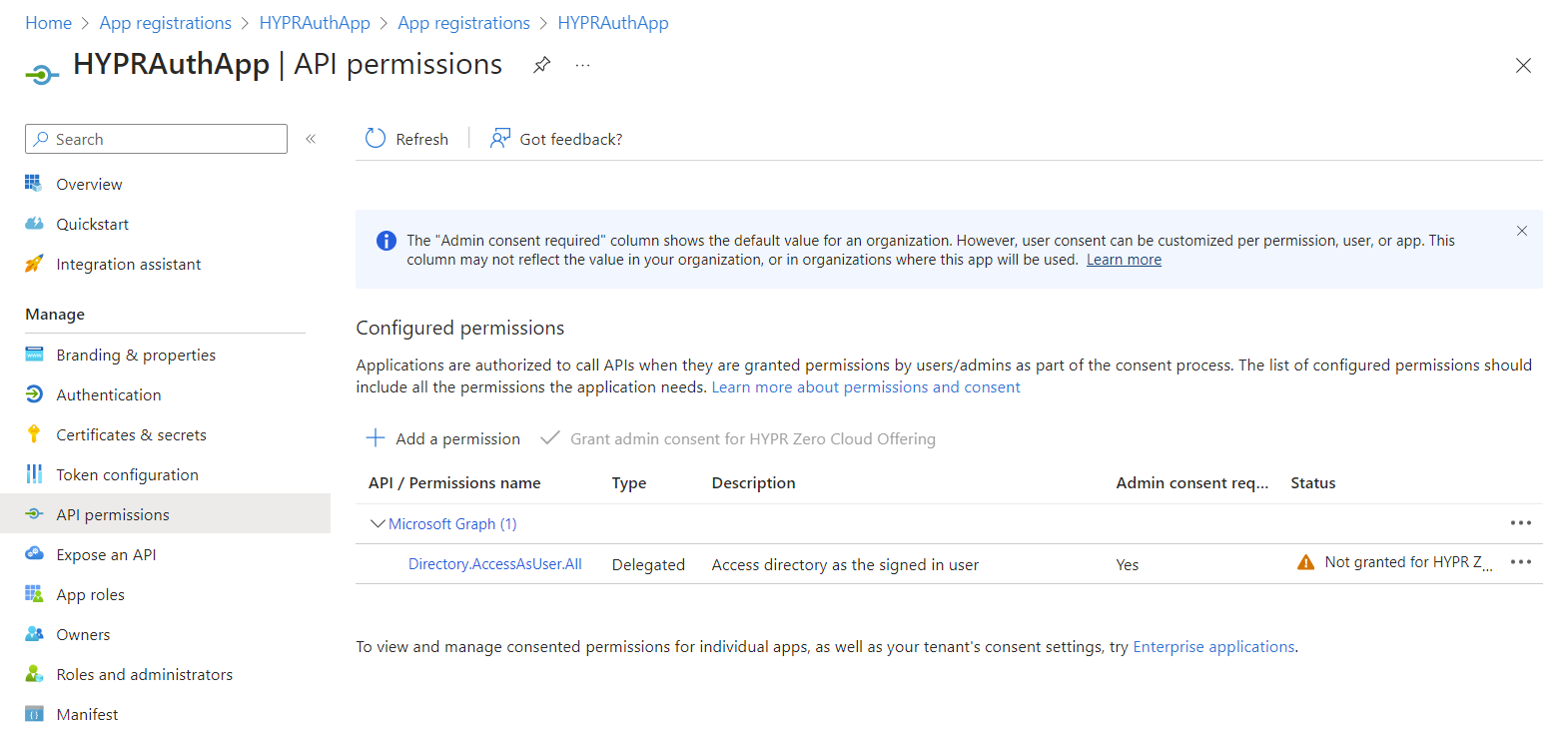
Now select Application permissions, locate and select the following permissions, then click Add Permissions:
-
User.ReadWrite.All -
Directory.ReadWrite.All
-
-
Verify admin consent as been granted (beside + Add a permission). If not, click Grant admin consent to apply the permissions and click Yes to confirm when prompted.
Creating an application credential
You'll need to provide a credential when you set up the integration in the HYPR Control Center, which is going to be used to interact with the Entra resources via the Graph API. You can use a client secret or a client certificate as this credential.
The Entra ID External Authentication Method integration uses the OAuth 2.0 Client Credentials Grant flow to authenticate to Entra's Graph API.
Using a client secret
If you choose to use a client secret, you can generate it in Entra ID as follows:
-
From the Entra ID screen, select App registrations and choose your app.
-
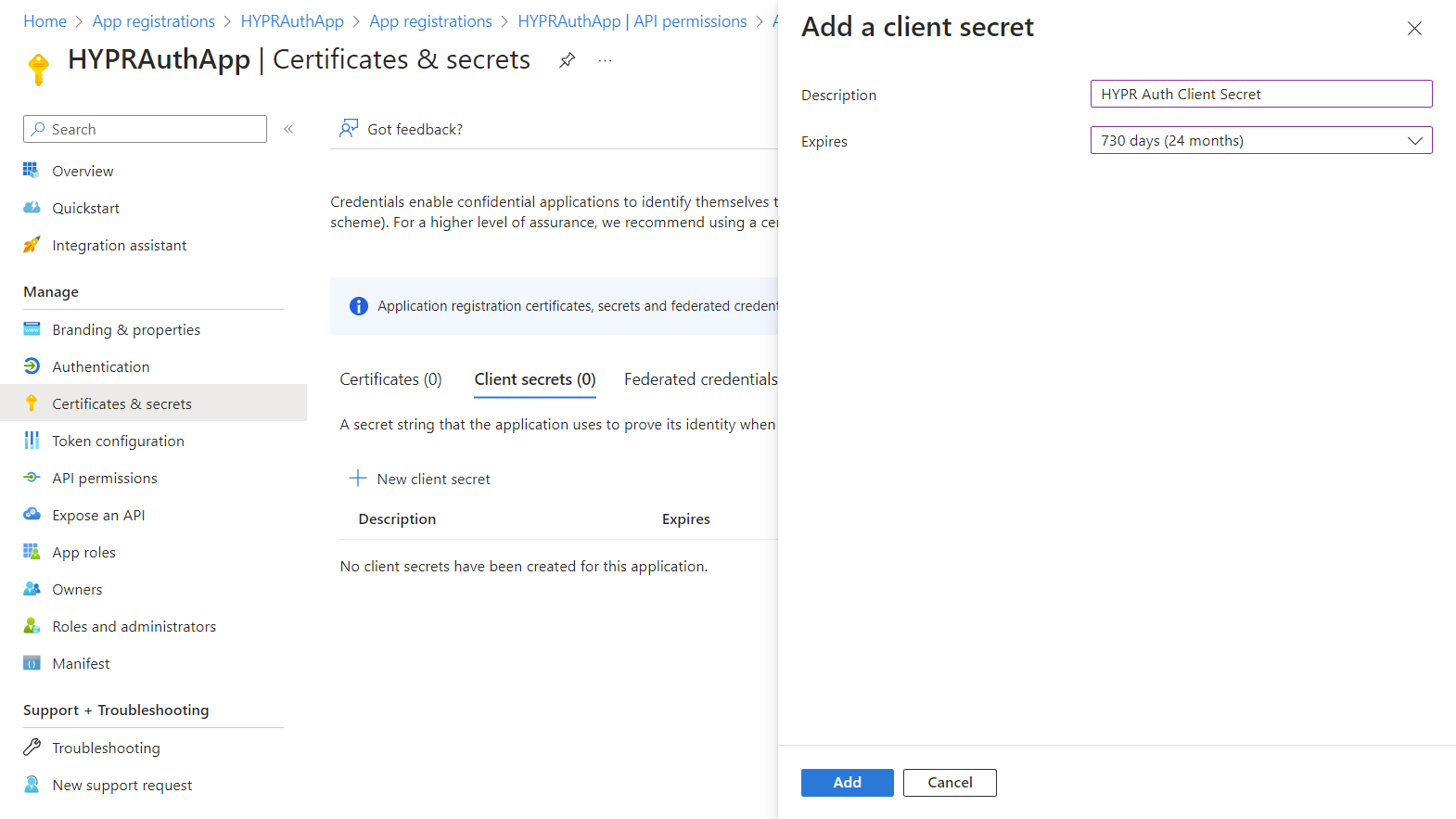
Select Certificates & secrets, then select Client secrets and click New client secret.
-
Enter a Description and an Expires date. Click Add when finished. Entra ID returns to the Certificates and Secrets list.
-
Make a note of the client secret value now so you can use it later.
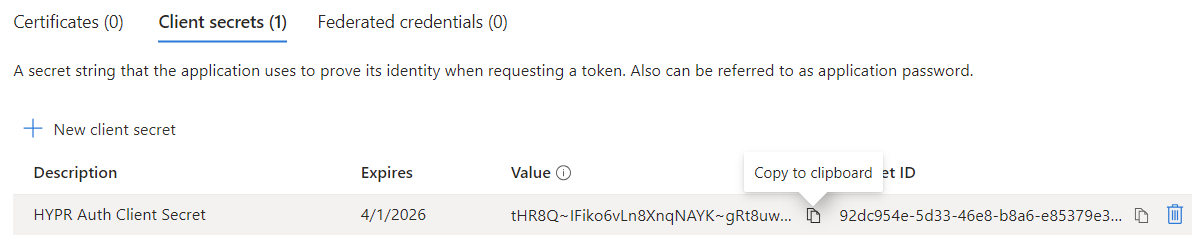
One Time OnlyIf you return to this screen later, Entra ID will mask the value and you won't be able to copy it.
Using a client certificate
If you choose to use a client certificate, you can upload it in Entra ID as follows:
-
From the Entra ID screen, select App registrations and choose your app.
-
Select Certificates & secrets, then select Certificates and click Upload certificate.
-
Enter a Description and click Add when finished. Entra ID returns to the Certificates and Secrets list.
You will need to have an X.509 certificate and its corresponding private key available if you decide to use client certificate-based authentication. The certificate can be a self-signed or signed by a Certificate Authority trusted by your organization.
For more information about the use of X.509 certificates in Entra ID applications refer to the corresponding guide. You can also check their guidance on usage of self-signed certificates.
HYPR Control Center - Connecting Entra ID to HYPR
Once Entra ID is set up, you can add the integration to HYPR.
-
Go to the Integrations screen in the HYPR Control Center and click Add New Integration to show a list of available integration types.
-
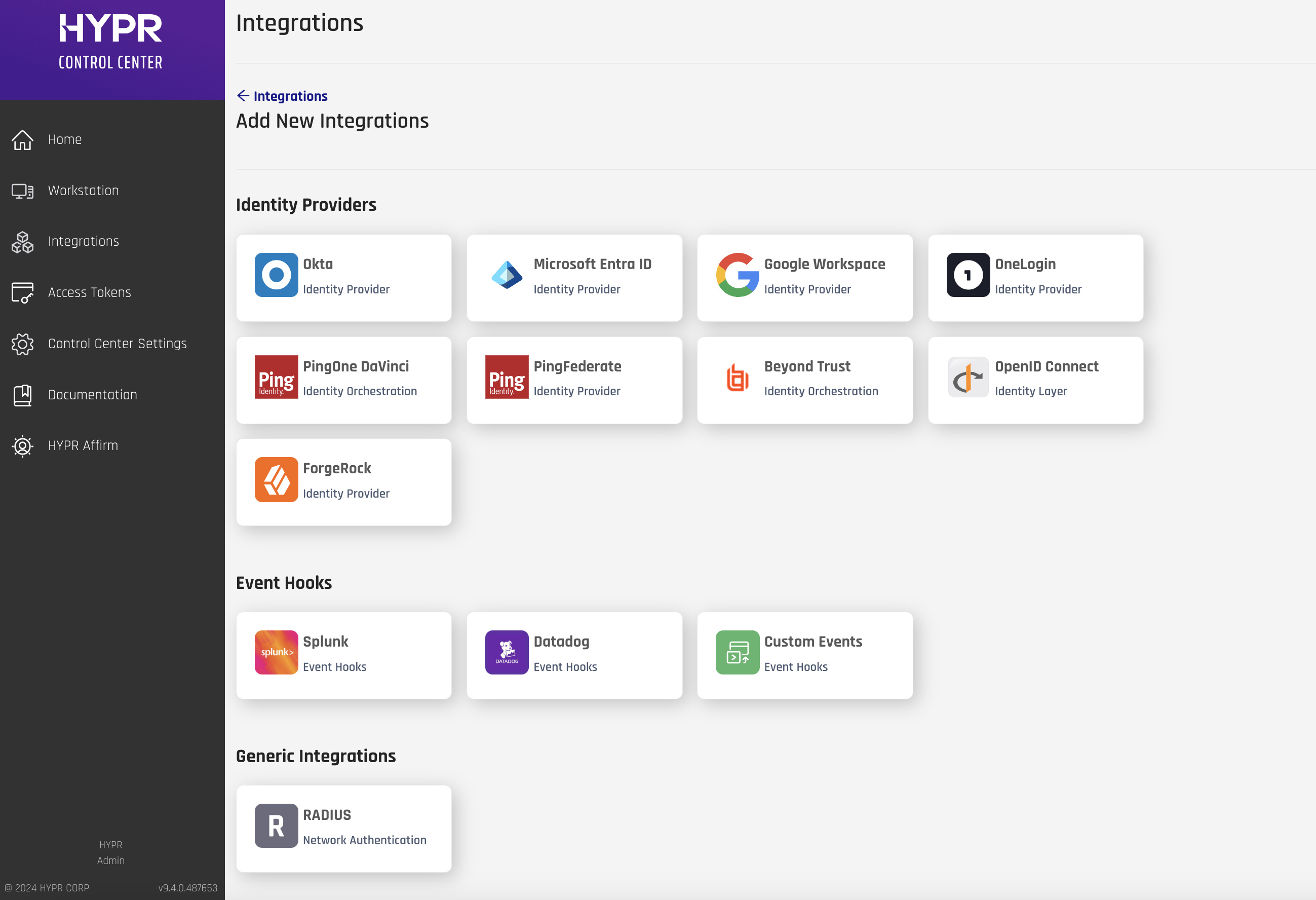
Select the Microsoft Entra ID integration.
-
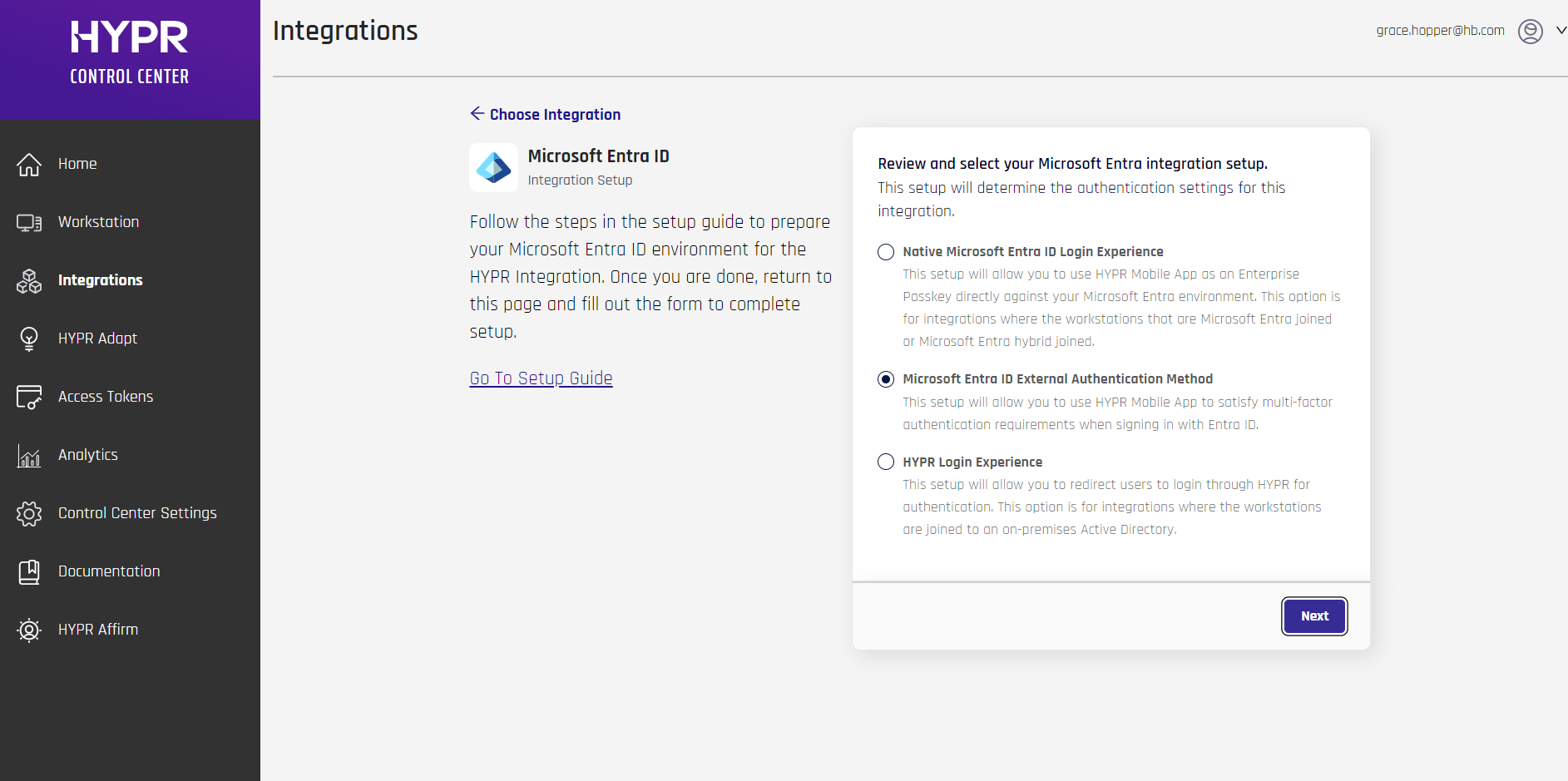
HYPR will present you with a choice; select Microsoft Entra ID External Authentication Method.
-
To integrate HYPR and Entra ID, you just need to provide some information on the HYPR Login Setup screen.
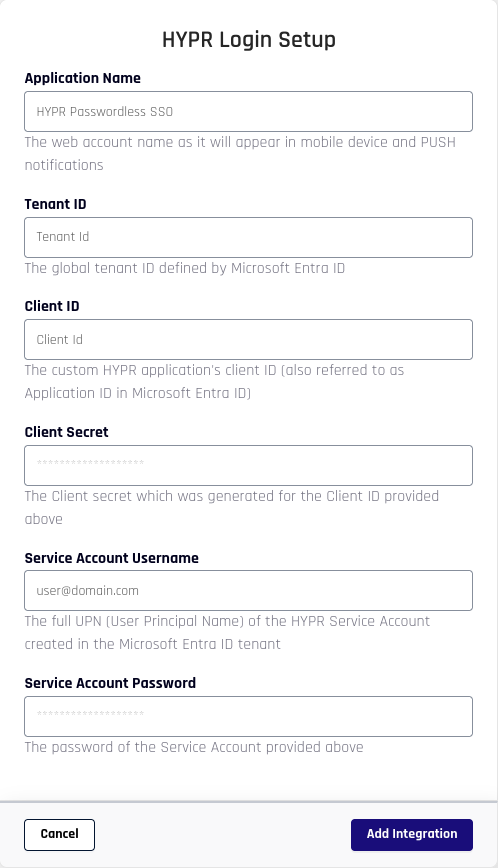
Field Value Application Name The name you provide here will be used in three places:
- For the web account name that users will see in the HYPR Mobile App
- For the HYPR Device Manager page where users register their devices
- For internal identification of this integration within the HYPR platform
You can use any name you like, but it's best to go with something that indicates the purpose of the application. For example:
passwordlessClientEntraSSO
You can use numbers, spaces, hyphens, and underscores in the name but note that spaces will be stripped from the name used to internally identify the integration within the HYPR platform. The namespace is limited to 23 characters.
This is the application name you'll also use when taking the last configuration steps in Entra ID.
Once set, the only way to change the Application Name is to delete and re-add the integration.Tenant ID The Directory (tenant) ID from Entra ID.
If you didn't make a note of this earlier, you can retrieve it from the Overview page for the application in Entra ID (see Registering the HYPR Entra ID Application).
Once set, the only way to change the Tenant ID is to delete and re-add the integration.Client ID The Application (client) ID from Entra ID.
If you didn't make a note of this earlier, you can retrieve it from the Overview page for the application in Entra ID (see Registering the HYPR Entra ID Application).
Once set, the only way to change the Client ID is to delete and re-add the integration.Client Secret The client secret value for the Entra ID application
If you didn't make a note of this earlier, you'll need to go back and generate a new one in Entra ID (see Using a Client Secret).Client Certificate The X.509 certificate uploaded to the Entra ID application, if you decided to use a client certificate.
You'll need to provide the certificate in PEM-encoded format.Client Private Key The private key of the client certificate uploaded to the Entra ID application, if you decided to use a client certificate.
You'll need to provide the private key in PEM-encoded format. -
Click Add Integration to begin.
-
If the setup succeeds, you'll see the Integration Added! confirmation dialog.
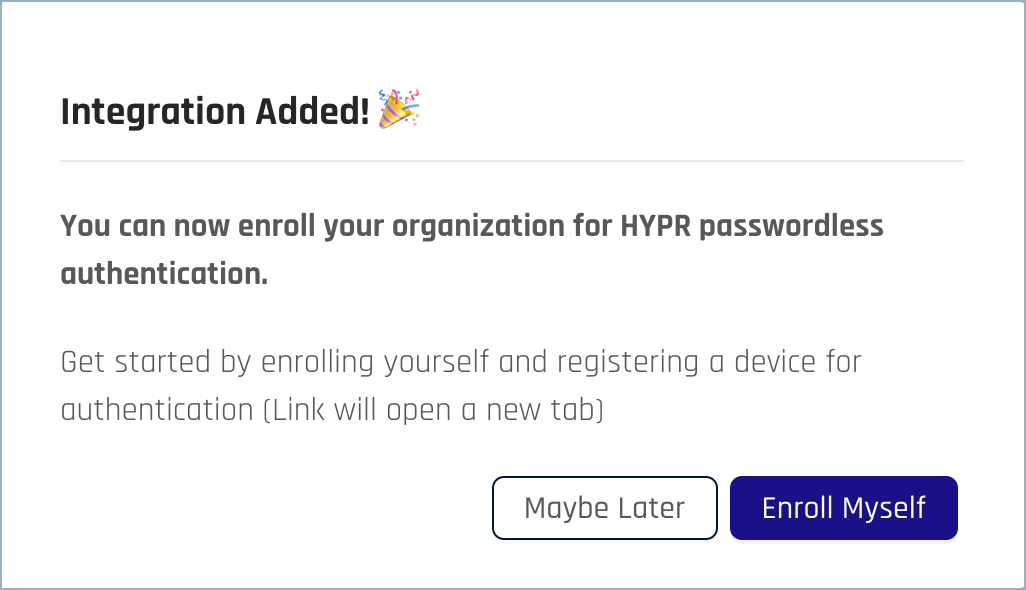
-
You can optionally now register to use HYPR Entra ID logins yourself by clicking Enroll Myself. You'll be taken to the HYPR Device Manager where you can register your mobile device.
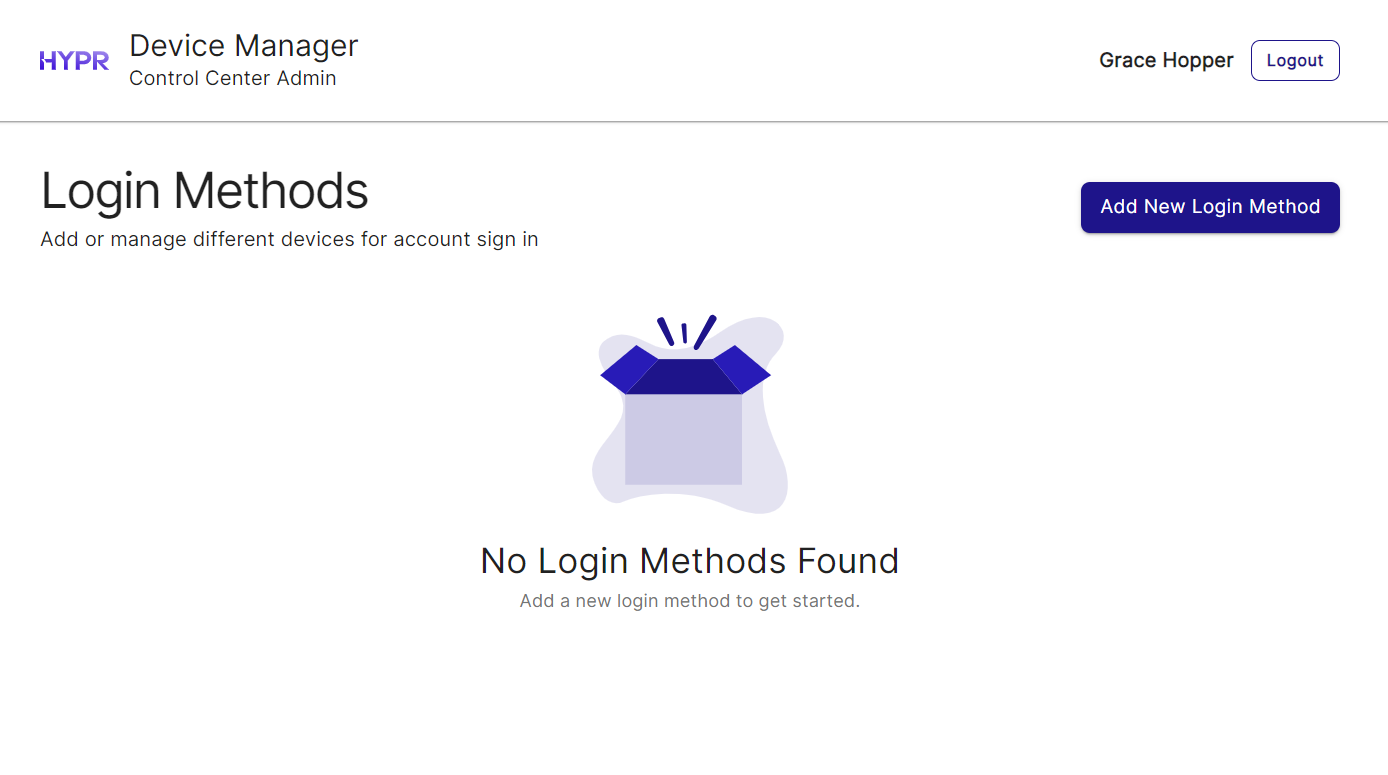
Self-enrollmentThe Enroll Myself option is only available if your Entra ID username is the same as your HYPR Control Center username. If they are not the same, you can add yourself to the Integration as a regular user later (see Enrolling Users).
-
Once you've registered a device, you'll see your username in the list of enrolled users.
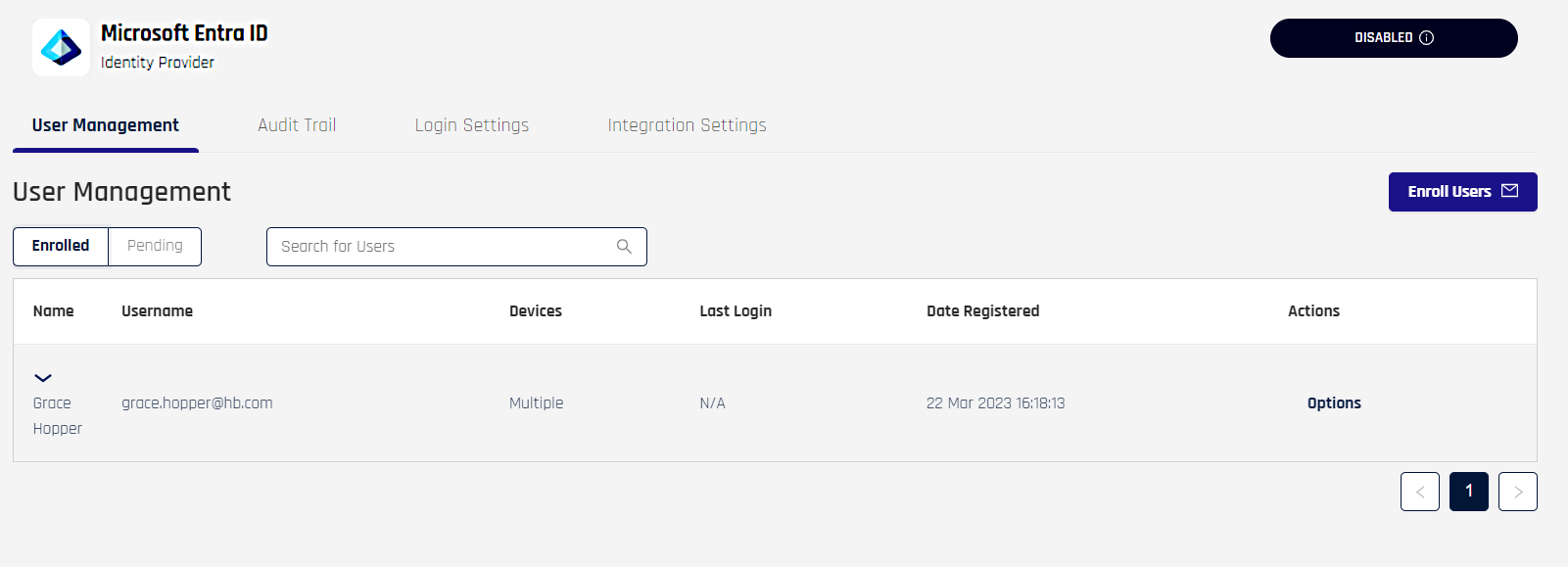
Back to Entra ID
Now for the final configuration steps, you'll need to complete the configuration on Entra ID
Application Authentication
-
Open the application you're using for the HYPR Entra ID External Authentication Method integration; then open Authentication.
-
Click Add a platform. A panel opens to the right. Click Web
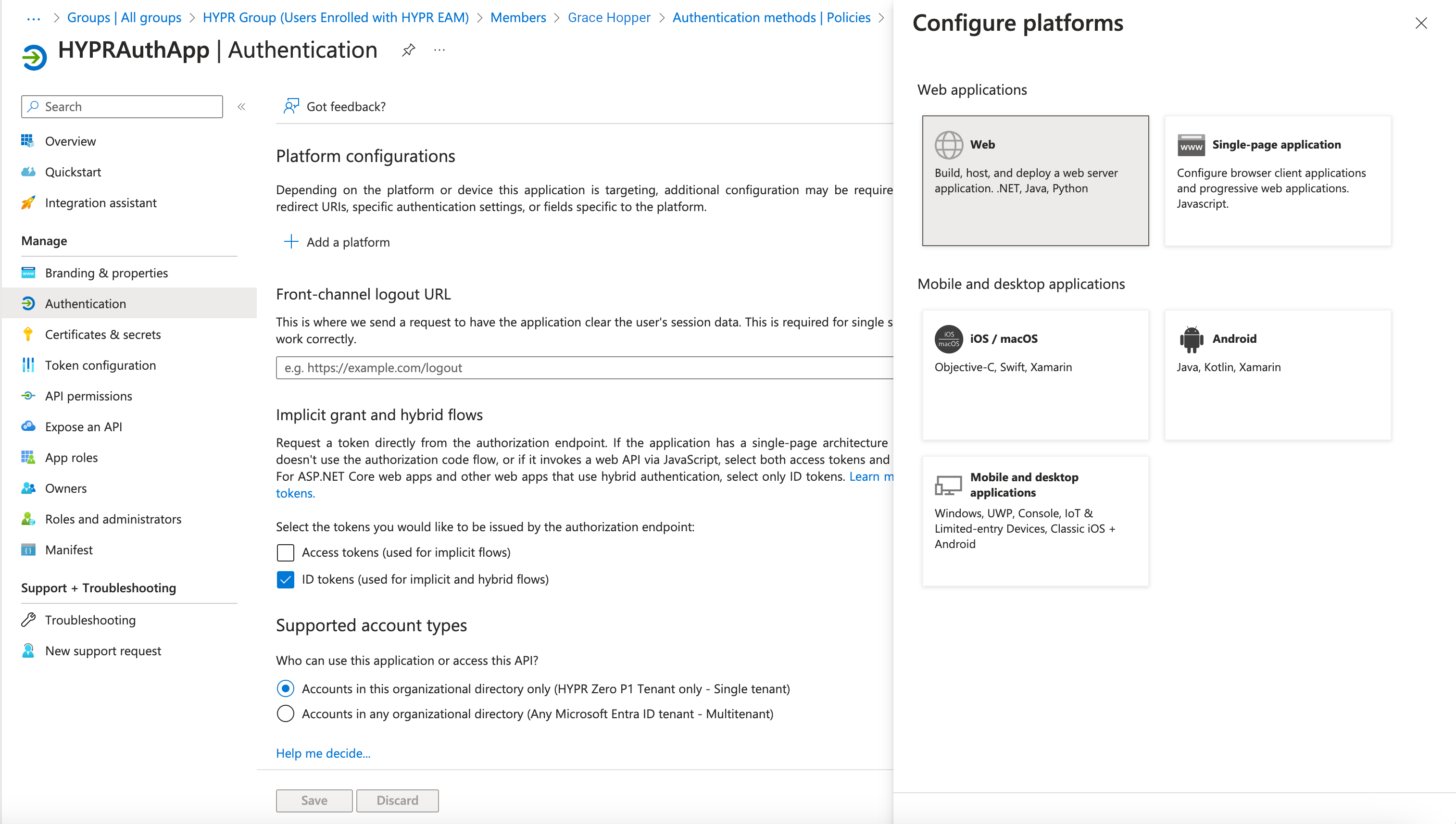
-
Type the redirect URL to which you will send EAM users; use the following format:
https://<HYPR Tenant ID>/auth/realms/externalauthmethods_<HYPR Application Name>/protocol/openid-connect/auth
<HYPR Tenant ID>is the base URL of your HYPR tenant, in this case highlandsbank.hypr.com<HYPR Application Name>is the name of the Application you created on HYPR Control Center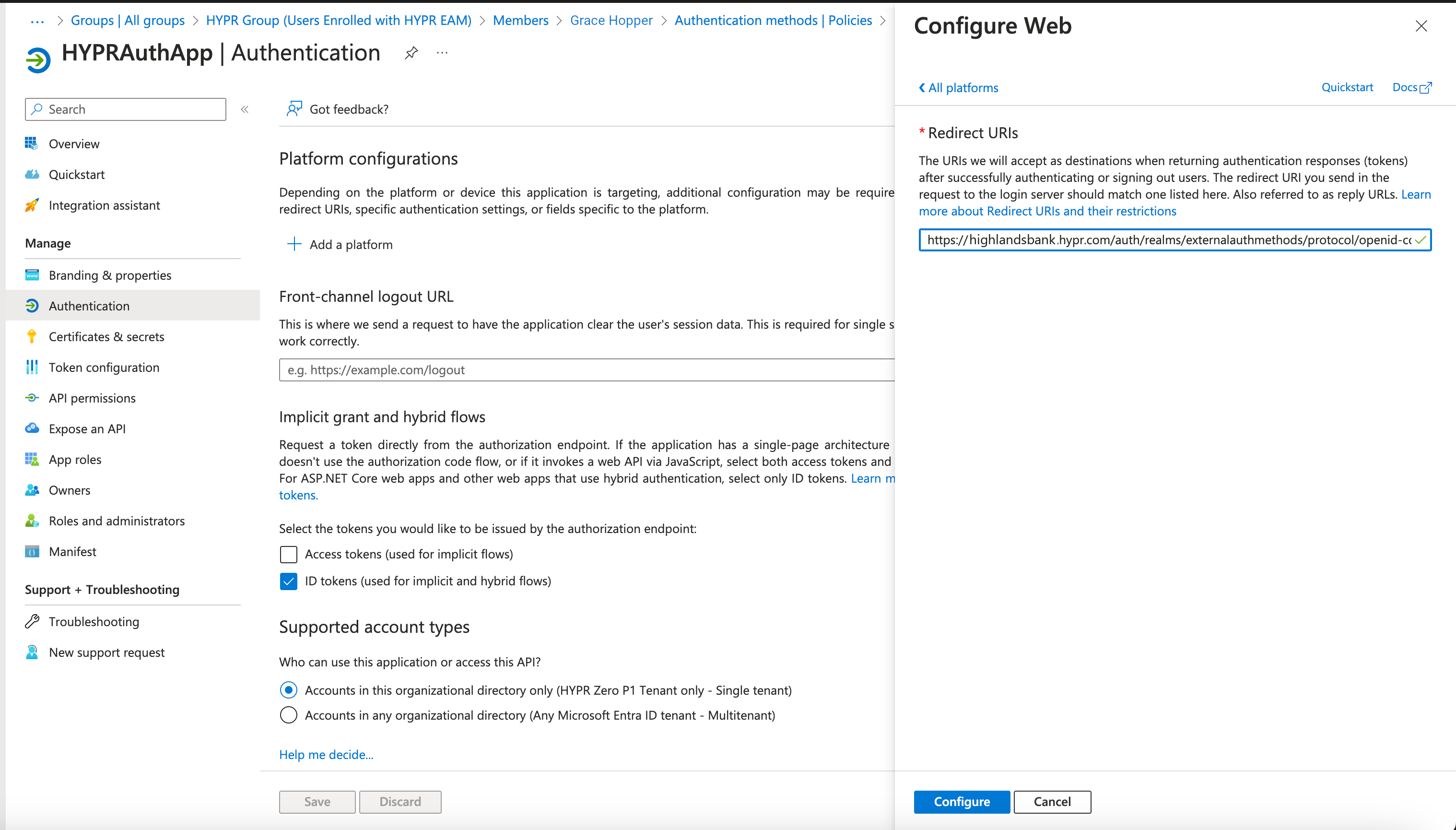
-
Click Configure when you are finished. Your platform configuration displays in the Authentication main pane.
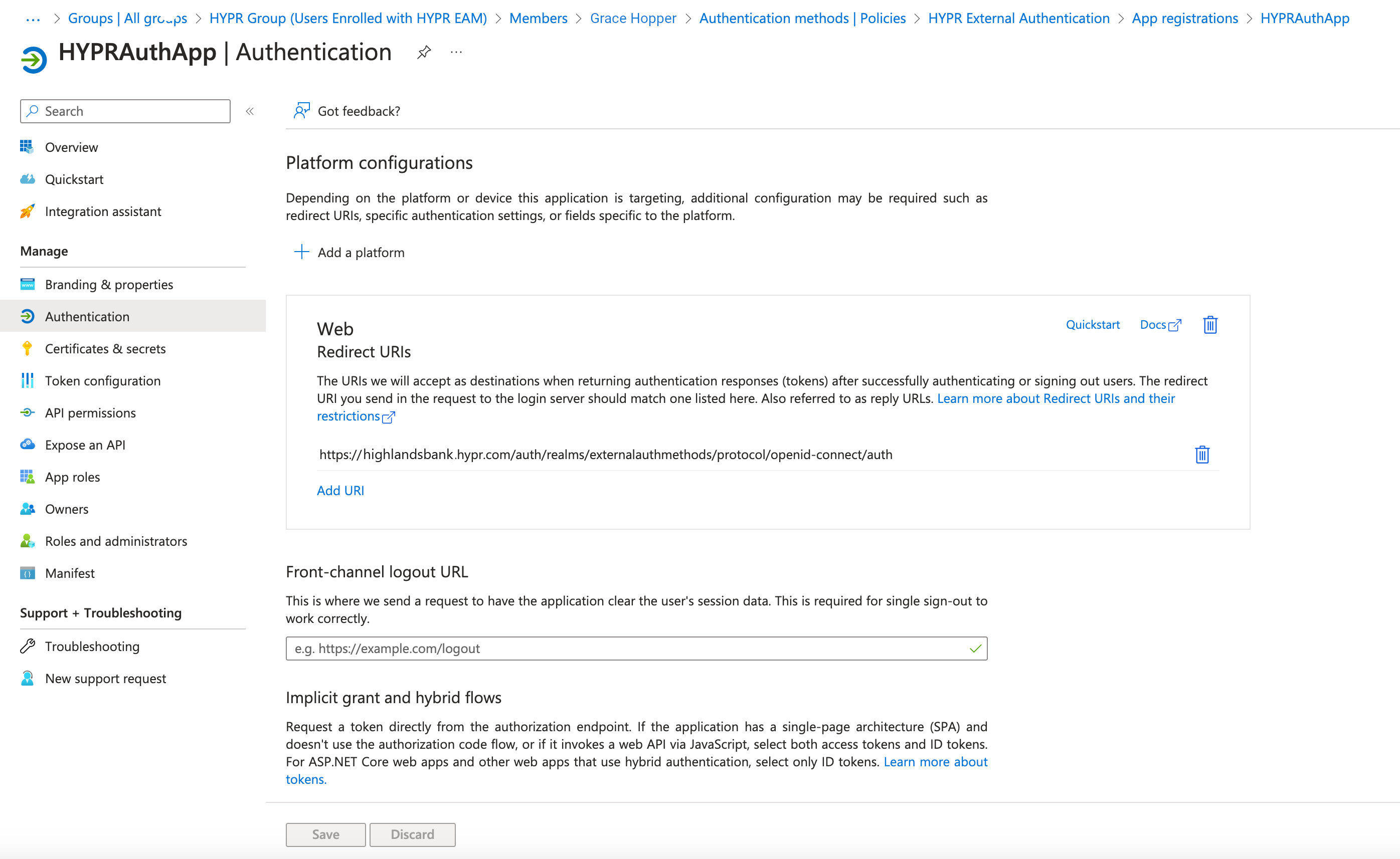
Create the External Authentication Method
-
Open your Entra ID tenant > Protection > Authentication methods > Policies.
-
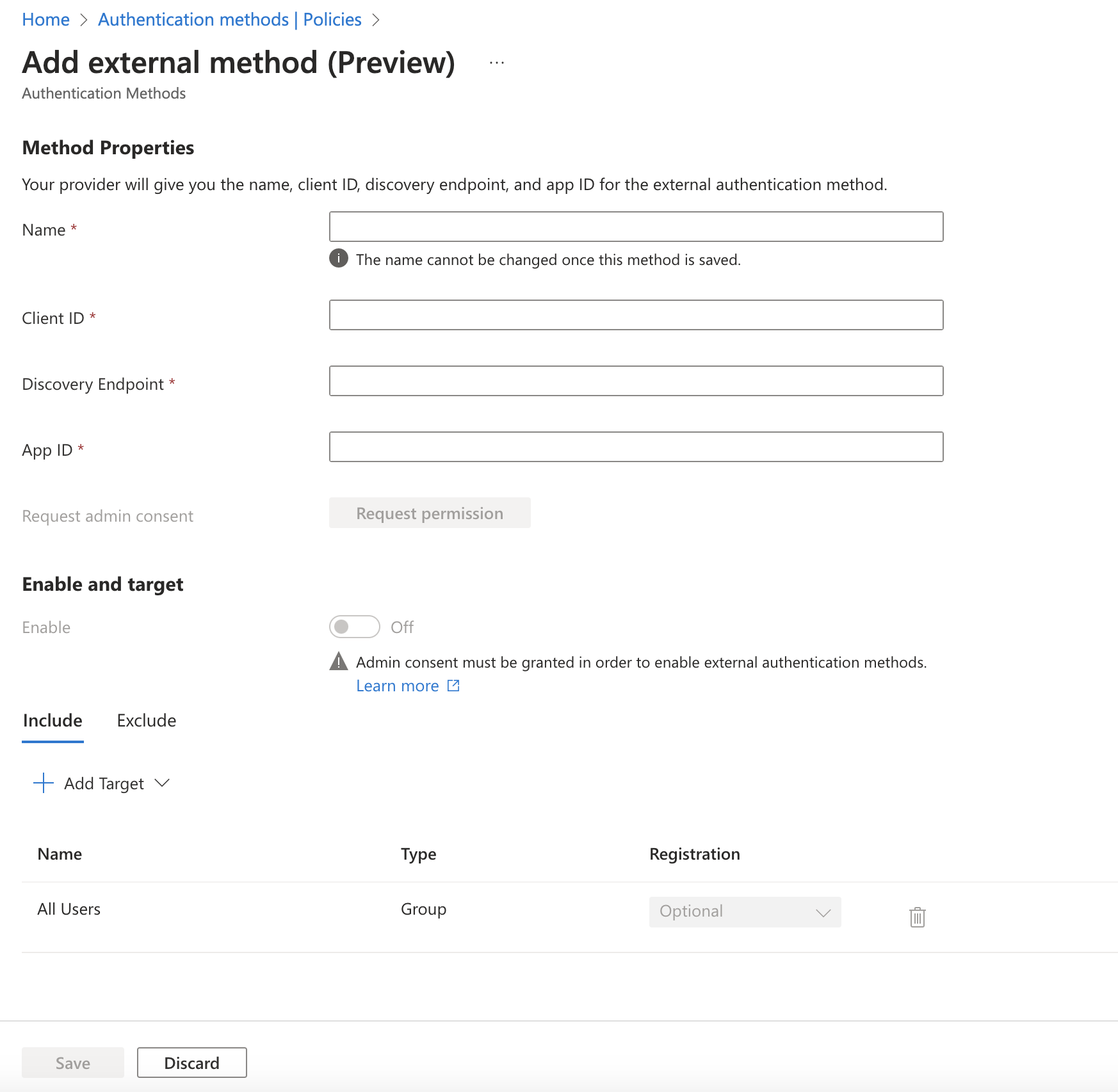
Click + Add external method (Preview). Complete the fields as follows:
-
Method Properties
Field Value Name HYPR External Authentication Client ID externalauthmethods Discovery Endpoint https://<HYPR Tenant ID>/auth/realms/externalauthmethods_<HYPR Application Name>/.well-known/openid-configurationApp ID The Application (client) ID value from the Entra ID application you want to use. <HYPR Tenant ID>is the base URL of your HYPR tenant, in this case highlandsbank.hypr.com<HYPR Application Name>is the name of the Application you created on HYPR Control Center -
Enable and target
Field Value Enable Off Include Click + Add Target and select the HYPR EAM group you wish to use.
-
-
Click Save when you are finished.
Enable MFA for the group of users
-
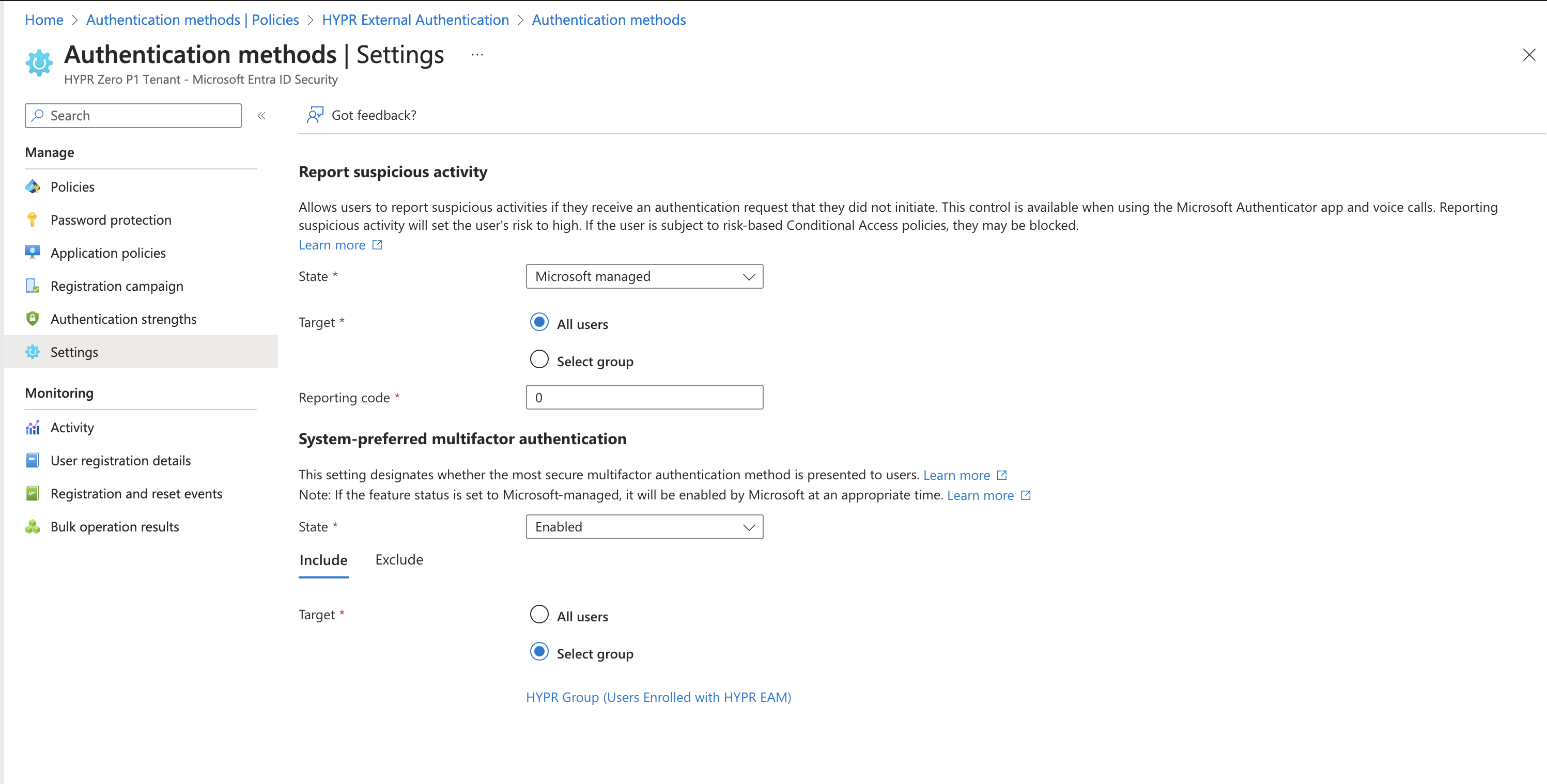
From the Entra ID portal home screen, select Protection > Authentication methods > Settings.
-
Configure the fields as follows:
-
System-preferred multifactor authentication
Field Value State Enabled Include: Target Select group: [Choose your HYPR EAM group]
-
-
Click Save when you are finished.
Set Conditional Access Policies
-
Open Microsoft Entra ID > Protection > Conditional access > Policies.
-
Click + New policy; assign the following values:
-
Give the policy a Name.
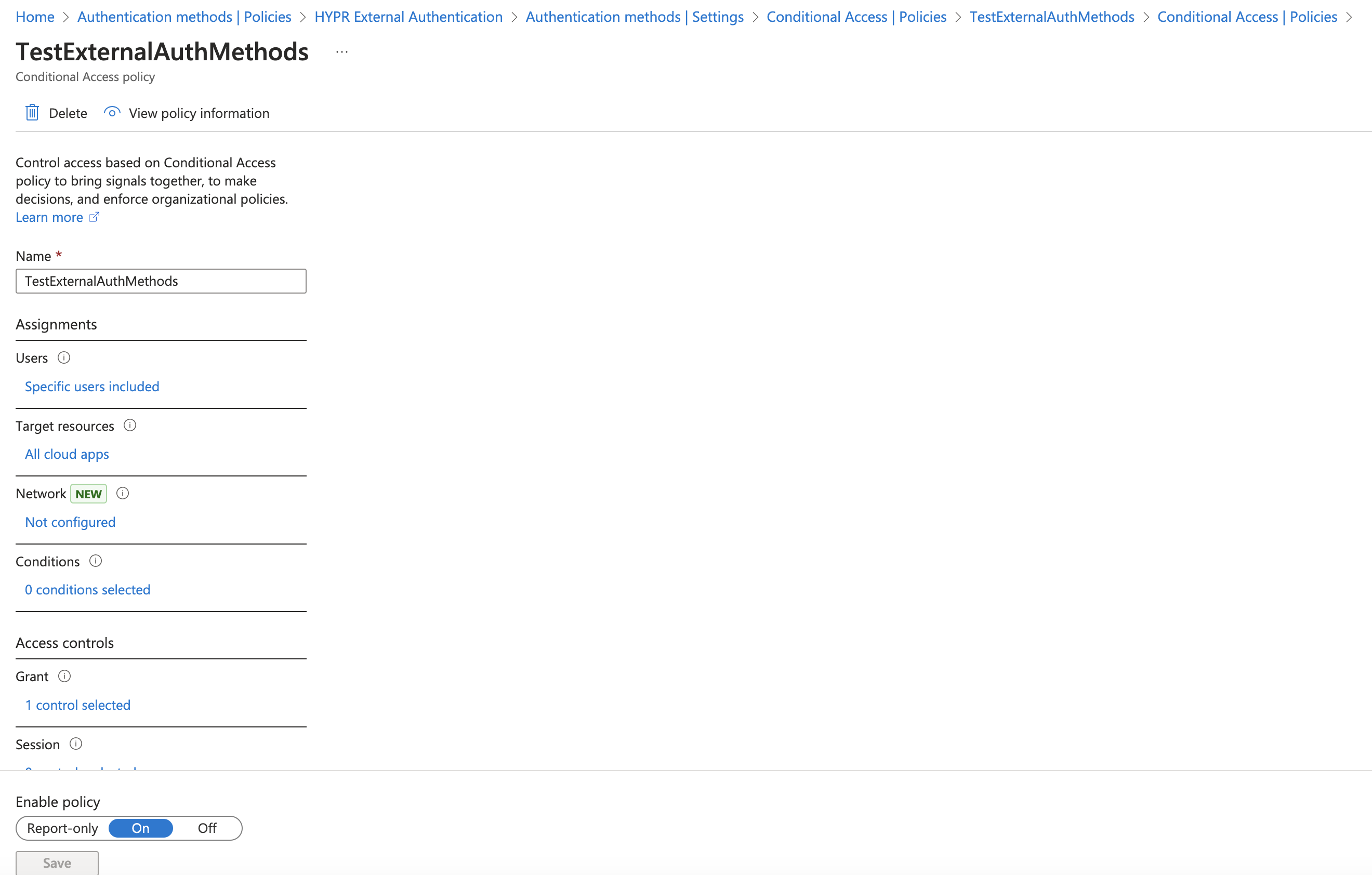
-
Under Assignments > Users > Include, choose Select users and groups and check the box next to Users and groups. Locate the HYPR EAM group you wish to use and select it.
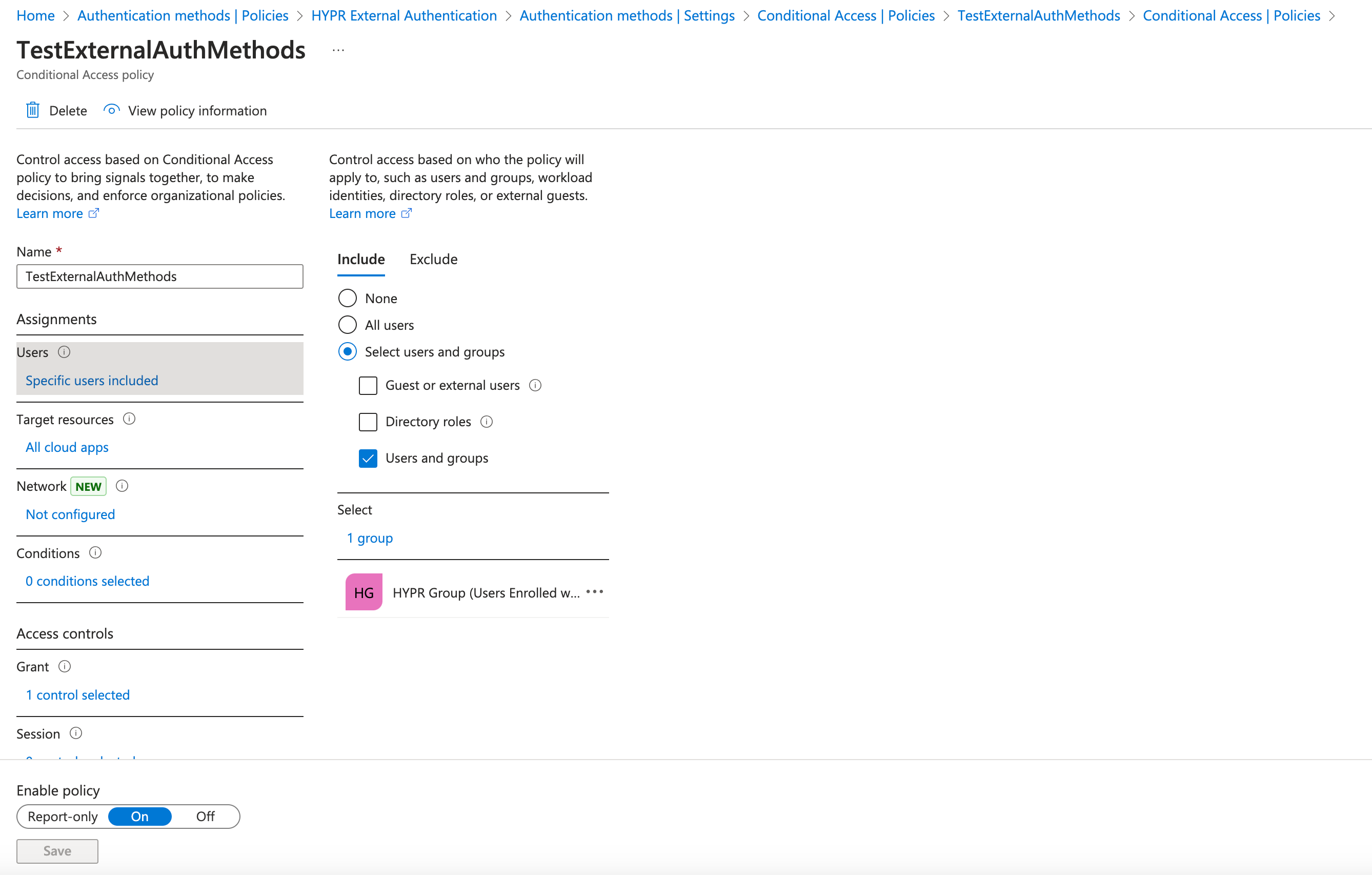
-
For Target resources, select All resources (formerly 'cloud apps') from the drop-down menu, then Include All resources (formerly 'All cloud apps').
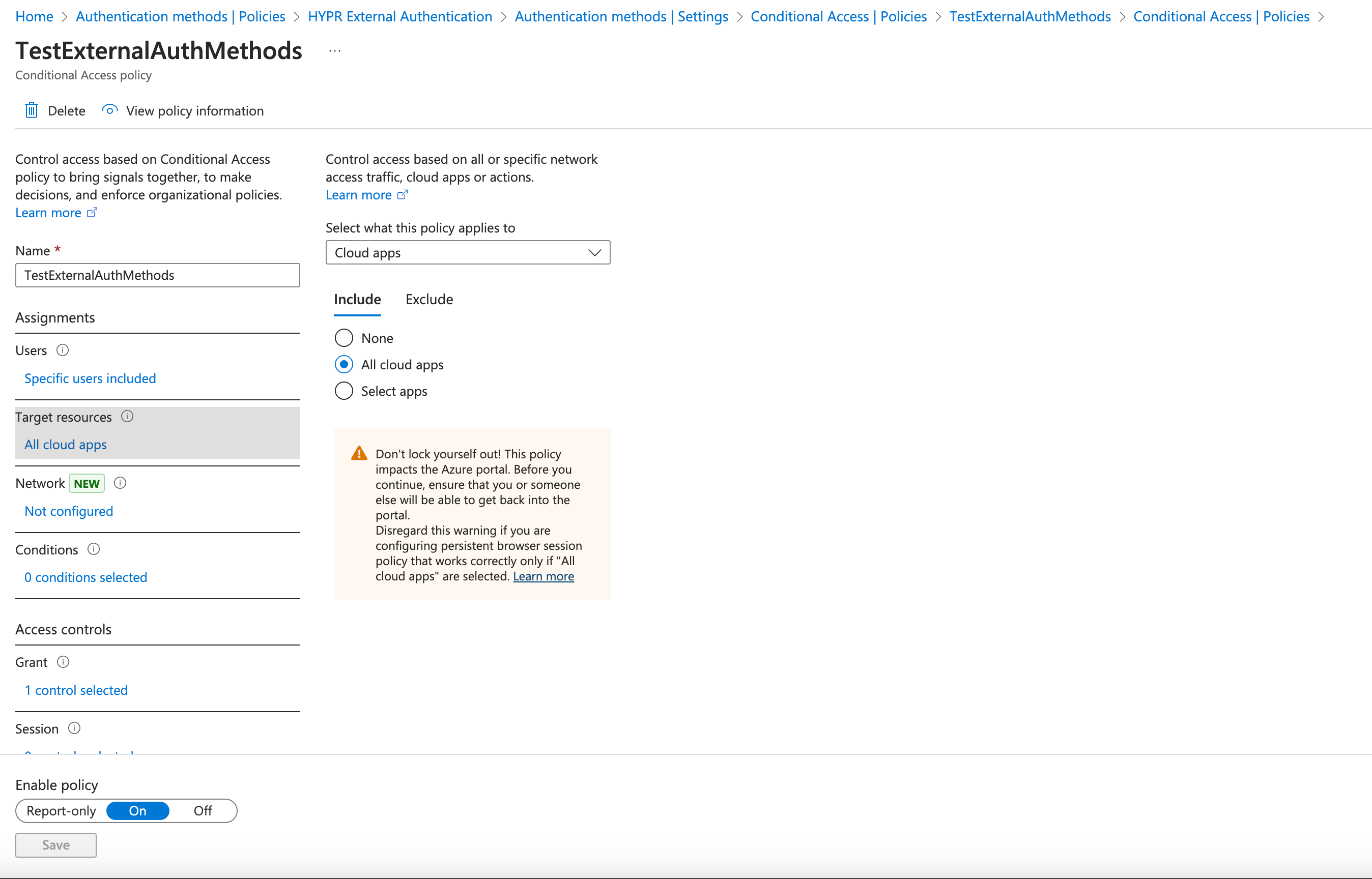
-
Set Grant to Grant access and check the box next to Require multifactor authentication; click Select when you are finished
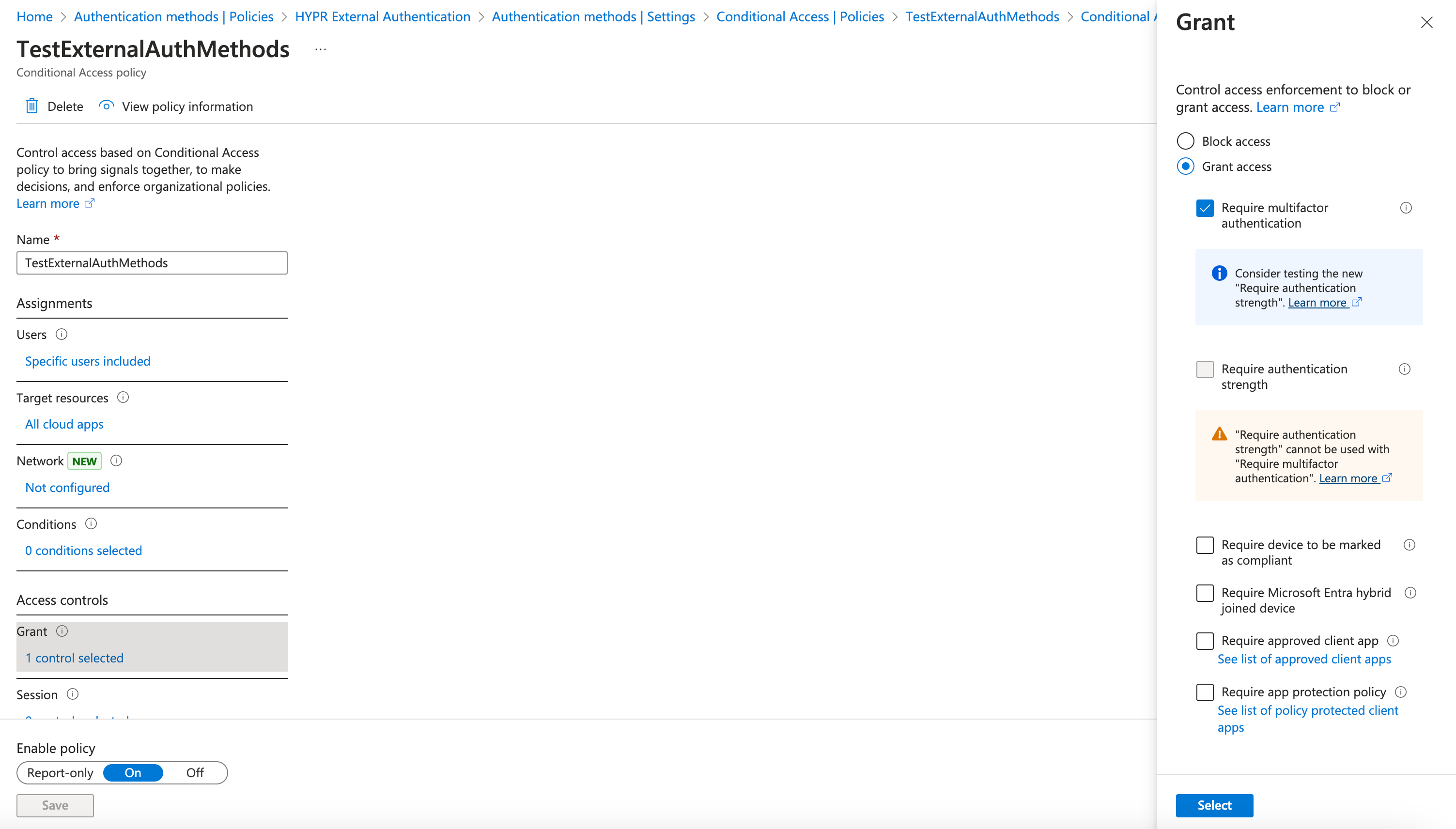
-
-
Ensure that Enable policy is On, then click Save at the bottom.
Continue with the HYPR Integrations common UI experience in the Integrations main page to complete Enabling your integration, enrolling users, and monitoring activity with the integration's Audit Trail.