Event Descriptions
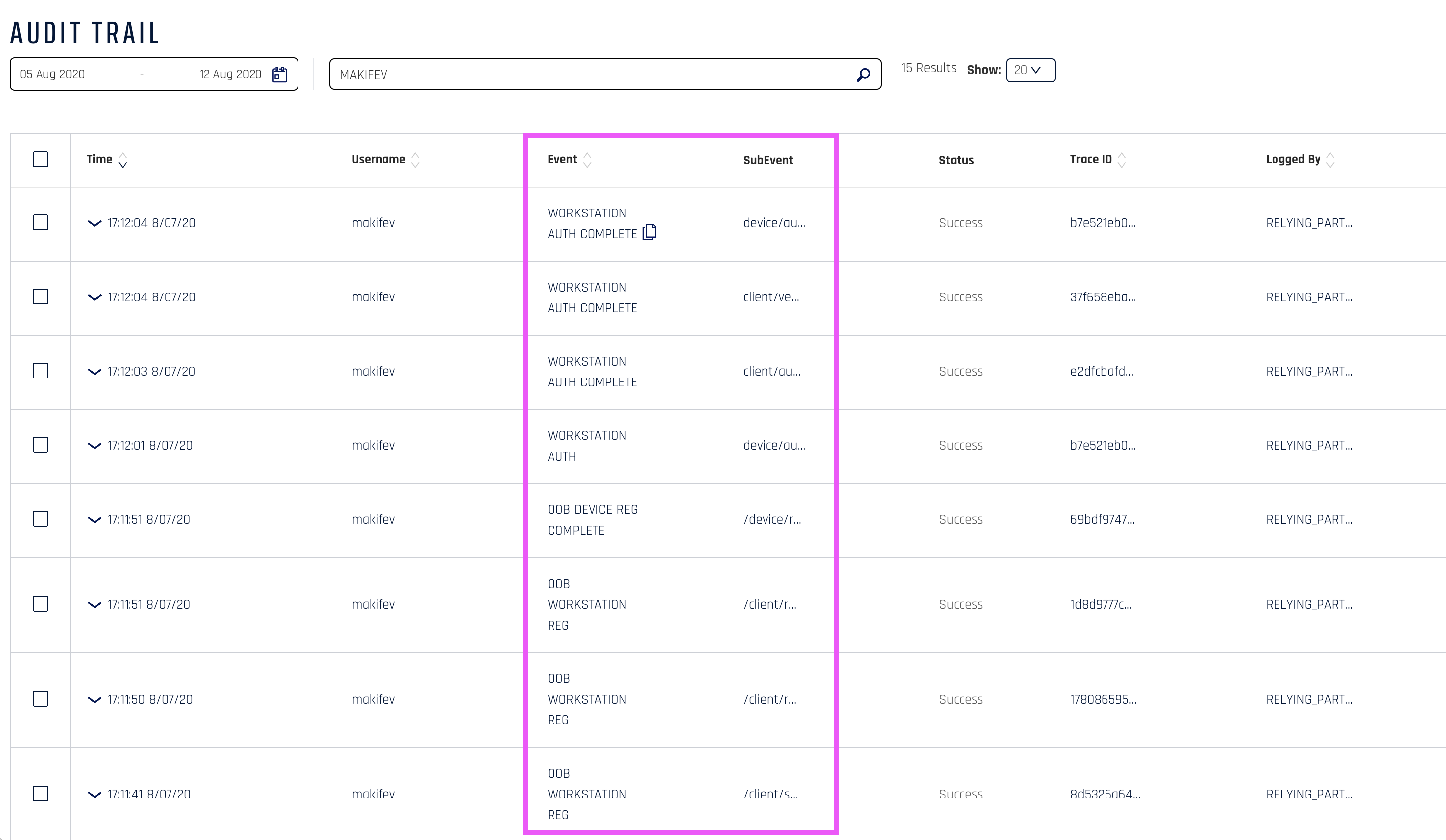
Each single captured Event is a result of a successful or failed attempt. Events appear in the Audit Trail, in the Control Center (CC) logs, in the HYPR Dashboard for Splunk, and in API call results.
Not every Event is listed in the CC Audit Trail or HYPR Dashboard for Splunk; some only appear in HYPR Passwordless API responses or CC logs.
Event data is stored in a separate schema away from the critical HYPR FIDO databases. This allows registration, authentication, and deregistration flows to continue functioning without being affected. The connection information to this schema can be found in the Vault; a HYPR representative can help you find it. The settings for the Audit Trail schema will be automatically set up for you during installation.
We anticipate that potentially millions of records could exist in this database. We have included a means to roll over the data. This mechanism will be described in detail at the bottom of this guide.
eventTags
Most Events fall under one of the following eventTags categories; those that do not are listed last. Table listings under the following categories are sorted by the Action column.
A list of Event Parameters follows the event descriptions.
ACCESS_TOKEN (ADMIN) Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| ACCESS_TOKEN_CREATE | ADMIN ACCESS_TOKEN | RELYING_PARTY_SERVER | Endpoint API token creation request; this event is typically from the the browser token management UI. |
| ACCESS_TOKEN_REVOKE | ADMIN ACCESS_TOKEN | RELYING_PARTY_SERVER | Endpoint API token revoked. tokenId=[token.id] revokedBy=[user] |
ADMIN Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| LOGIN | ADMIN | CONTROL_CENTER_SERVER | The user logged in to Control Center. |
| LOGOUT | ADMIN | CONTROL_CENTER_SERVER | Logout from Control Center web console. |
| FIDO2_METADATA | ADMIN | CONTROL_CENTER_SERVER | FIDO2 metadata statement with AAGUID modified. aaguid = [aaguid] |
| CREATE_INTEGRATION | ADMIN | RELYING_PARTY_SERVER | Successfully added an IdP integration. |
| DELETE_INTEGRATION | ADMIN | RELYING_PARTY_SERVER | Successfully deleted the IdP integration. |
| DISABLE_INTEGRATION | ADMIN | RELYING_PARTY_SERVER | Successfully disabled the IdP integration. |
| ENABLE_INTEGRATION | ADMIN | RELYING_PARTY_SERVER | Successfully enabled the IdP integration. |
| REFRESH_INTEGRATION | ADMIN | RELYING_PARTY_SERVER | Successfully refreshed the IdP integration. OR Failed to refresh the IdP integration. |
| SUSPEND_INTEGRATION | ADMIN | RELYING_PARTY_SERVER | Successfully suspended the IdP integration. |
| UPDATE_INTEGRATION | ADMIN | RELYING_PARTY_SERVER | Successfully updated the IdP integration details. |
| AUTHENTICATOR_DISABLED | ADMIN | CONTROL_CENTER_SERVER | The authenticator was disabled for this rpAppId. Authentication requests using this authenticator will fail. aaid=[aaid] rpAppId=[appId] |
| AUTHENTICATOR_ENABLED | ADMIN | CONTROL_CENTER_SERVER | The authenticator was enabled. aaid=[aaid] rpAppId=[rpAppId] |
| UAF_FACETID_ADDED | ADMIN | CONTROL_CENTER_SERVER | The FIDO FacetID was added. |
| UAF_FACETID_REMOVED | ADMIN | CONTROL_CENTER_SERVER | The FIDO FacetID was removed. |
| CREATE_APP | ADMIN | CONTROL_CENTER_SERVER | |
| [rpAppId] was succesfully created. | |||
| CREATE_APP_ACTION | ADMIN | [Not Logged] | An authentication or registration policy was created for [rpAppId]. |
| DELETE_APP | ADMIN | CONTROL_CENTER_SERVER | Associated settings have been deleted. |
| DELETE_APP_ACTION | ADMIN | CONTROL_CENTER_SERVER | Delete action for [rpAppId]. |
| DELETE_APP_CONFIG | ADMIN | RELYING_PARTY_SERVER | RP Application configuration has been deleted. config: [config.toStringTruncateValue()] |
| SAVE_APP_CONFIG | ADMIN | RELYING_PARTY_SERVER | The Application configuration was saved. One or more of the following changed: - Theme color, logo, title, or messaging - Push and/or QR enablement toggle - Desktop SSO enablement toggle - Timeout configuration |
| UPDATE_APP | ADMIN | CONTROL_CENTER_SERVER | [rpAppId] was succesfully updated. |
| UPDATE_APP_ACTION | ADMIN | CONTROL_CENTER_SERVER | Update action for [rpAppId]. |
| USERNAME_DISSOCIATE | ADMIN | RELYING_PARTY_SERVER | All associations with an email or alias have been deleted. |
| USERNAME_ASSOCIATE | ADMIN | RELYING_PARTY_SERVER | The username has been associated with [this]. |
AUTHENTICATION Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| DESKTOP_SSO | AUTHENTICATION WORKSTATION | RELYING_PARTY_SERVER WORKSTATION | Desktop SSO started by web login attempt. |
| DESKTOP_SSO_COMPLETE | AUTHENTICATION | RELYING_PARTY_SERVER WORKSTATION | Desktop SSO completed by the workstation signing challenge. |
| EXTERNAL_AUTH_COMPLETE | AUTHENTICATION (OOB | Browser | DM | Java SDK) WORKSTATION | RELYING_PARTY_SERVER | Workstation [unlock | login] using [deviceType]. |
| FALLBACK_AUTHENTICATOR | AUTHENTICATION WORKSTATION | MobileDevice | Fallback authentication has been [ enabled | disabled ] . |
| FIDO_ONLY_AUTH | AUTHENTICATION MOBILE_DEVICE | UAF_SERVER | FIDO authentication using the cryptographic key. |
| FIDO_ONLY_TRANS | AUTHENTICATION MOBILE_DEVICE | RELYING_PARTY_SERVER | |
| FIDO2_WEBAUTHN | AUTHENTICATION MOBILE_DEVICE | RELYING_PARTY_SERVER | A web authentication (webAuthn) attempt was made. |
| FIDO2_WEBAUTHN_COMPLETE | AUTHENTICATION MOBILE_DEVICE | RELYING_PARTY_SERVER | Web authentication (webAuthn) with [aaguid] was successful. OR Mobile device: Authentication as a platform authenticator or with a security key plugged into the mobile device. This is the use case where the browser running on the mobile device does WebAuthn with the Relying Party. |
| HYPR_GATEWAY_WORKSTATION_DRIVER | AUTHENTICATION WORKSTATION | Workstation | A workstation became able to communicate with a device capable of Enterprise Passkey Authentication. |
| HYPR_GATEWAY_AVAILABLE | AUTHENTICATION | Server | The server is configured to accept a device and workstation Enterprise Passkey Authentication. |
| HYPR_MOBILE_DATABASE | AUTHENTICATION MOBILE_DEVICE | MobileDevice | The mobile device is reporting information on registrations prior to an Enterprise Passkey Authentication. |
| OOB_WEBSITE_AUTH | AUTHENTICATION (OOB | Browser | DM | Java SDK) KEYCLOAK | RELYING_PARTY_SERVER WEB MobileDevice | The browser requests authentication from the HYPR server for the user. A push notification is sent to the mobile device asking it to authenticate. A sessionId is generated and returned as a part of the response. Typical problems: - Network conditions may create delays in receiving the push notification |
| OOB_WEBSITE_AUTH_COMPLETE | AUTHENTICATION (OOB | Browser | DM | Java SDK) | RELYING_PARTY_SERVER | The client polls the server periodically to check if the mobile authentication is successful. The server returns the current status of authentication in the response message. |
| OOB_WEBSITE_TRANS | AUTHENTICATION (OOB | Browser | DM | Java SDK) MOBILE_DEVICE | RELYING_PARTY_SERVER MobileDevice | The browser requested authentication for a step transaction from the HYPR server. The HYPR server sent a push notification to the mobile device, asking it to authenticate. |
| QR_FALLBACK_PAYLOAD_CACHED | AUTHENTICATION | CONTROL_CENTER_SERVER | QR code was successfully cached for manual retrieval via QR Fallback deviceId=null, rpAppId=[rpAppId] |
| QR_FALLBACK_PAYLOAD_RETRIEVED | AUTHENTICATION | CONTROL_CENTER_SERVER RELYING PARTY_SERVER | [Success] Cached payload was retrieved using the respective activation code associated with creation. \n \n[Failure] Failed to find QR fallback payload using activation code provided. Please check code entered and retry. |
| SESSION_WEBSITE_AUTH | AUTHENTICATION MOBILE_DEVICE | MobileDevice | Authentication was attempted using a QR code. |
| SESSION_WEBSITE_AUTH_COMPLETE | AUTHENTICATION | [Not Logged] | Authentication was completed using a QR code. |
| WEBSITE_AUTH | AUTHENTICATION | MobileDevice | Operation/Authentication canceled/failed. |
| WORKSTATION_AUTH | WORKSTATION_AUTH AUTHENTICATION MOBILE_DEVICE WORKSTATION | RELYING_PARTY_SERVER MobileDevice Workstation | Start of the workstation unlock request from the device. This request is made when the user clicks the Unlock button in the HYPR App. A message is sent to the workstation to initiate unlock/login. |
| WORKSTATION_AUTH_COMPLETE | WORKSTATION_AUTH AUTHENTICATION | RELYING_PARTY_SERVER | Final confirmation that workstation unlock is successful. Client and device top off the offline tokens. |
| WORKSTATION_AUTH_COMPLETE | WORKSTATION_AUTH | RELYING_PARTY_SERVER | The client has finished unlocking the workstation. The login confirmation message reached the workstation. Completed. |
| WORKSTATION_AUTH_COMPLETE | WORKSTATION_AUTH | RELYING_PARTY_SERVER | The user has verified their physical presence at the workstation. Generally, this involves pressing Ctrl+Alt+Delete. |
| UNIVERSAL_QR_SCAN | AUTHENTICATION | MobileDevice | Operation canceled. The HYPR barcode scan was aborted by the user. |
| WORKSTATION_AUTH_JSON_SCAN | AUTHENTICATION MOBILE_DEVICE | MobileDevice | A mobile device was used to initiate a workstation lock or unlock event. |
| WORKSTATION_AUTH_QR_SCAN | AUTHENTICATION MOBILE_DEVICE | [Not logged] | A mobile device has been paired with a workstation via QR scan. |
CREATE_USER, DELETE_USER Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| DELETE_USER | DELETE_USER | RELYING_PARTY_SERVER | [userName] was deleted from the Control Center using the API token belonging to [userPerformingDelete]. [if no devices left] [userName] has no remaining registrations after removing [deviceId]. Deleting the user record. |
| MAGIC_LINK_CREATE_USER | ADMIN MAGIC_LINK | RELYING_PARTY_SERVER | [userName] was invited to Control Center via magic link and email. |
DEREGISTRATION Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| MOBILE_INITIATED_WEBSITE_DELETE | Delete | RELYING_PARTY_SERVER MobileDevice | A deregistration request was initiated from a mobile device for a website. The mobile user clicked on the Delete Web Account button. |
| MOBILE_INITIATED_WORKSTATION_DELETE | DEREGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER MobileDevice | A deregistration request was initiated from a mobile device for a workstation. The mobile user clicked on the Delete Computer button. |
| OOB_WEBSITE_INITIATED_DELETE | DEREGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER | A deregistration request was initiated from the web account or Control Center. |
| OOB_DEVICE_UNPAIRED (was WORKSTATION_INITIATED_DELETE) | DEREGISTRATION MOBILE_DEVICE WORKSTATION | RELYING_PARTY_SERVER Workstation MobileDevice | A deregistration request was initiated from the workstation. The user clicked on the Delete Mobile Device button in the HYPR app on the computer. |
| FIDO_ONLY_DEREG | DEREGISTRATION MOBILE_DEVICE | UAF_SERVER MobileDevice WEB | FIDO registration is deleted. It can no longer be used to authenticate. |
| FIDO2_DEVICE_DEREG | DEREGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER | FIDO2 key [aaid] deleted for user [userName]. |
| FIDO2_DEVICE_RESET | DEREGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER | [FIDO2 key [aaid] reset for user [userName]. |
| MOBILE_INITIATED_WORKSTATION_UNPAIRED | DEREGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER | A deregistration request was initiated from a mobile device for a workstation. The mobile user clicked on the Delete Computer button. |
ENDPOINT_API_ACCESS_TOKEN (ADMIN) Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| ENDPOINT_API_ACCESS_TOKEN_CREATE | ADMIN ENDPOINT_API_ACCESS_TOKEN | RELYING_PARTY_SERVER | The endpoint API token was created. Scope = [DEVICE | WORKSTATION] tokenId = [truncated_token] |
| ENDPOINT_API_ACCESS_TOKEN_EXCHANGE | ADMIN ENDPOINT_API_ACCESS_TOKEN | RELYING_PARTY_SERVER | The workstation install token was successfully exchanged. tokenId=[truncated_token] |
| ENDPOINT_API_ACCESS_TOKEN_EXCHANGE_FAILED | ADMIN ENDPOINT_API_ACCESS_TOKEN MOBILE_DEVICE WORKSTATION | RELYING_PARTY_SERVER MobileDevice | The workstation install token exchange failed. tokenId=[truncated_token] |
| ENDPOINT_API_ACCESS_TOKEN_REVOKE | ADMIN ENDPOINT_API_ACCESS_TOKEN | RELYING_PARTY_SERVER | The endpoint API token was successfully revoked. tokenId=[token.id] revokedBy=$user |
ERROR Events
Event (eventName) | Action | Source (eventLoggedBy) | Description ( message) |
|---|---|---|---|
| EXCEPTION | ERROR KEYCLOAK MOBILE_DEVICE WORKSTATION | RELYING_PARTY_SERVER | Captures any oddities that may occur on the mobile, workstation, or web components. |
FEATURE_FLAGS (ADMIN) Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| FEATURE_FLAG_TOGGLE | ADMIN FEATURE_FLAGS | RELYING_PARTY_SERVER | Feature Flag toggled. |
IDENTITY VERIFICATION (IdV) Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| AFFIRM_APPLICATION_CONFIGURATION_CHANGED | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm Configuration changed - [Onboarding | Recovery] flow. |
| AFFIRM_WORKFLOW_ATTESTATION | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Attestation. |
| AFFIRM_WORKFLOW_ATTESTATION_OUTCOME_TYPE | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Outcome type. |
| AFFIRM_WORKFLOW_CHAT_ESCALATION | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - chat escalation |
| AFFIRM_WORKFLOW_CONVERSATION | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Conversation. |
| AFFIRM_WORKFLOW_DOCUMENT_UPLOAD | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Document upload. |
| AFFIRM_WORKFLOW_EMAIL_CODE_SENT | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - code sent. |
| AFFIRM_WORKFLOW_FACE_MATCH | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Face match. |
| AFFIRM_WORKFLOW_IDV_FINISH | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - IDV finish. |
| AFFIRM_WORKFLOW_IDV_START | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - IDV start. |
| AFFIRM_WORKFLOW_INVITE_SENT | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - [Approver |Secondary Approver] invite sent. |
| AFFIRM_WORKFLOW_LOCATION | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Location. |
| AFFIRM_WORKFLOW_PHONE_NUMBER_ENTERED | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Phone number entered. |
| AFFIRM_WORKFLOW_RESULT | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Attestation. |
| AFFIRM_WORKFLOW_STARTED | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Workflow started. |
| AFFIRM_WORKFLOW_TEXT_CODE_SENT | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Text code sent. |
| AFFIRM_WORKFLOW_TEXT_CODE_VERIFIED | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Text code verified. |
| AFFIRM_WORKFLOW_VIDEO | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Video. |
| AFFIRM_WORKFLOW_VIDEO_APPROVER_ENABLED | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Video Approver Enabled. |
| AFFIRM_WORKFLOW_VIDEO_REQUESTER_ENABLED | IDENTITY_VERIFICATION | RELYING_PARTY_SERVER | Affirm workflow event - Video Requester Enabled. |
KEYCLOAK Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| KEYCLOAK_ADMIN_EVENT | AUTHENTICATION KEYCLOAK | WEB | [Variable JSON output.] |
| KEYCLOAK_POSSIBLE_BRUTE_FORCE_AUTH_ATTEMPT | AUTHENTICATION (OOB | Browser | DM | Java SDK) KEYCLOAK | WEB | Users latest authentication attempt triggered brute force detection. Will eventually block user temporarily if this keeps occuring. |
| KEYCLOAK_USER_EVENT | AUTHENTICATION KEYCLOAK | WEB | [Variable JSON output.] |
| KEYCLOAK_USER_TEMPORARILY_DISABLED | AUTHENTICATION (OOB | Browser | DM | Java SDK) KEYCLOAK | RELYING_PARTY_SERVER | user: REDACTED is temporarily disabled by brute force detection |
MAGIC_LINK Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| MAGIC_LINK_CREATE | Magic Links | CONTROL_CENTER_SERVER RELYING_PARTY_SERVER | Magic link created. |
| MAGIC_LINK_DELETE | ADMIN MAGIC_LINK | CONTROL_CENTER_SERVER | Deleting pending magic links for: username=[userName] rpAppId=[rpAppId] |
| MAGIC_LINK_EXP_DELETE_EXISTING_AFTER_NEW | ADMIN MAGIC_LINK | CONTROL_CENTER_SERVER | Deleting existing magic links after creating new a one for the same username. |
| MAGIC_LINK_EXP_DELETED_EXISTING | ADMIN MAGIC_LINK | CONTROL_CENTER_SERVER | Pre-existing magic links have been deleted. Only one magic link can be alive at a given time. |
| MAGIC_LINK_EXP_RESEND_EMAIL_MSG_TO_HAAS | ADMIN MAGIC_LINK | CONTROL_CENTER_SERVER | An invitation email has been generated and sent to [userName]. |
| MAGIC_LINK_EXP_USERNAME_NOT_FOUND | ADMIN MAGIC_LINK | CONTROL_CENTER_SERVER | Username not found. Unable to resend an email to HYPR with a new magic link message. |
| MAGIC_LINK_EXPIRED_OR_USED | ADMIN MAGIC_LINK | RELYING_PARTY_SERVER | This magic link is invalid or has expired. |
| MAGIC_LINK_NOT_FOUND | ADMIN MAGIC_LINK | CONTROL_CENTER_SERVER | Cannot find a magic link for the token given. Verify that the token is correct and try again. |
| MOBILE_DYNAMIC_LINK_USED | AUTHENTICATION REGISTRATION MOBILE_DEVICE | MobileDevice | Firebase from app open. HYPRLink from HYPR scan. Firebase from HYPR scan. |
MISCELLANEOUS Events (no eventTags)
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| WESBITE_AUTH | AUTHENTICATION | MobileDevice | Operation failed. Your request to authenticate this device didn't complete in time. Fingerprint timeout reached. Try again. |
| MOBILE_CERTIFICATE_REENROLLMENT | REGISTRATION MOBILE_DEVICE WORKSTATION | RELYING_PARTY Workstation MobileDevice | The certificate was re-issued by the enrollment service. |
| DEFAULT | Core System | [Not Logged] | A default entry for anomalous events. |
| UNKNOWN | Core System | [Not Logged] | EventName= [name] is not known to this version of the server. The event may have been introduced in a newer version of the server. |
| LOG_SUBMISSION | ERROR | CONTROL_CENTER_SERVER RELYING_PARTY_SERVER | [clientType] client logs were submitted successfully. OR [clientType] client logs were submitted successfully by [userName]. OR WINDOWS client logs were submitted successfully by [machineUserName]. |
| AUTH_DENIED_LOW_VERSION | ERROR REGISTRATION | [Not Logged] | Authentication was denied due to a prohibitively low version of Control Center. |
| REG_DENIED_LOW_VERSION | ERROR REGISTRATION | [Not Logged] | Registration was denied due to a prohibitively low version of Control Center. |
| MOBILE_INITIATED_WORKSTATION_LOCK | Workstation-related | [Not Logged] | The mobile device initiated a workstation lock action. |
OFFLINE_ACCESS Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| OFFLINE_TOKEN_ACCESS | Workstation-related | MobileDevice | Offline token access request. |
| OFFLINE_TOKEN_AUTH | Workstation-related | Workstation | Authentication using Offline Mode. A mobile app user used an Offline Mode PIN to login to the workstation. |
POV Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| MOBILE_DYNAMIC_LINK_USED | AUTHENTICATION REGISTRATION MOBILE DEVICE | RELYING_PARTY_SERVER | [ HYPRlink | Firebase] from [ hypr scan | app open ]. |
| POV_EXPIRATION_CLEARED | POV | RELYING_PARTY_SERVER | POV expiration has been cleared. |
| POV_EXPIRATION_SET | POV | RELYING_PARTY_SERVER | POV has been set to expire on [friendlyDate]. |
RADIUS Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| RADIUS_CLIENT_CREATE | RADIUS | CONTROL_CENTER_SERVER | The Radius server client was created. id=[radiusClientId] |
| RADIUS_CLIENT_DELETE | RADIUS | CONTROL_CENTER_SERVER | The Radius server client was deleted. id=[radiusClientId] |
| RADIUS_CLIENT_UPDATE | RADIUS | CONTROL_CENTER_SERVER | The Radius server client was updated. id=[radiusClientId] |
| RADIUS_CONFIG_CREATE | RADIUS | CONTROL_CENTER_SERVER | The Radius server configuration was created. id=[configCreated.radiusConfigId] |
| RADIUS_CONFIG_DELETE | RADIUS | CONTROL_CENTER_SERVER | The Radius server configuration was deleted. id=[radiusConfigId] |
| RADIUS_CONFIG_UPDATE | RADIUS | CONTROL_CENTER_SERVER | The Radius server configuration was updated. id=[updatedConfig.radiusConfigId] |
| RADIUS_INTEGRATION_CREATE | RADIUS | CONTROL_CENTER_SERVER | The Radius integration was created. id=[createdIntegration.id] |
| RADIUS_INTEGRATION_DELETE | RADIUS | CONTROL_CENTER_SERVER | The Radius integration was deleted. id=[radiusIntConfigId] |
| RADIUS_ONBOARDED | RADIUS | CONTROL_CENTER_SERVER | Radius integration onboarded. id=[newIntegration.id] |
| RADIUS_SERVER_CREATE | RADIUS | CONTROL_CENTER_SERVER | The Radius server was created. id=[createdServer.radiusServerId] |
| RADIUS_SERVER_DELETE | RADIUS | CONTROL_CENTER_SERVER | The Radius server was deleted. id=[radiusServerId] |
| RADIUS_SERVER_UPDATE | RADIUS | CONTROL_CENTER_SERVER | The Radius server was updated. id=[radiusServerId] radiusConfigId=[radiusServer.radiusConfigId] |
RECOVERY_PINS (ADMIN) Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| RECOVERY_PIN_AUTH | ADMIN RECOVERY_PINS WORKSTATION | Workstation | Authorization was attempted using a recovery PIN. |
| RECOVERY_PIN_REVEAL | ADMIN RECOVERY_PINS | CONTROL_CENTER_SERVER RELYING_PARTY_SERVER | The recovery PIN was revealed via either the CC Admin UI or an API call. |
| RECOVERY_PINS_DELETE | ADMIN RECOVERY_PINS WORKSTATION | [Not Logged] | The recovery PIN was deleted. HYPR recommends generating new recovery PINS. |
| RECOVERY_PINS_GENERATED | ADMIN RECOVERY_PINS | RELYING_PARTY_SERVER | The recovery PIN has been saved. |
| RECOVERY_PINS_RE_GENERATED | ADMIN RECOVERY_PINS WORKSTATION | RELYING_PARTY_SERVER | The recovery PINs have been re-saved. |
| RECOVERY_PINS_SETUP | ADMIN RECOVERY_PINS | [Not Logged] | Recovery PINS were created. |
REGISTRATION Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| FIDO_ONLY_REG | REGISTRATION MOBILE_DEVICE | UAF_SERVER MobileDevice WEB | FIDO registration. The registration policy is supplied by the server. The device generates a cryptographic key pair, then sends the public key to the server. The user provides a second factor (touch/PIN/native/etc.) to safeguard the key. Typical problems: - The Application's policy(-ies) is not configured properly in Control Center - The authenticator specified by the policy is not available on the phone |
| FIDO2_DEVICE_REG | REGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER | User [userName] initiated FIDO2 key registration. |
| FIDO2_DEVICE_REG_COMPLETE | REGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER | A successful platform or security key registration was attempted on a mobile device. The browser running on the mobile device used WebAuthn with the Relying Party. Success: FIDO2 key registered Failure: Session not found for challenge , [expired | false]. Please contact HYPR customer support and report this issue. ExceptionId: |
| OOB_DEVICE_REG | REGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER MobileDevice | The device scans the QR code and sends starts the registration process. A sessionId is generated and returned as a part of the response. The initial handshake between the client (browser/workstation) is now complete. Typical problems: - PIN mismatch due to a timeout - Multiple scans of the same QR code |
| OOB_DEVICE_REG_COMPLETE | REGISTRATION | RELYING_PARTY_SERVER | The device QR scan registration process is complete. |
| OOB_DEVICE_PAIRED (was OOB_DEVICE_REG_COMPLETE) | REGISTRATION | RELYING_PARTY_SERVER | This is the final step in the registration process. Confirmation was received from the Device. The device registration record has been saved. |
| OOB_DEVICE_PAIRED (was OOB_DEVICE_REG_COMPLETE) | REGISTRATION | RELYING_PARTY_SERVER | The device started registration successfully. The PIN has been matched successfully. The Relying Party connection is OK. The device can now proceed to attempt a FIDO registration. |
| OOB_DEVICE_PAIRED (was OOB_DEVICE_REG_COMPLETE) | REGISTRATION | RELYING_PARTY_SERVER | A successful FIDO authentication was completed on a mobile device. Use traceId to match this event with the WORKSTATION_AUTH authentication start. traceId=[traceId] |
| OOB_GET_REG_DEVICES | REGISTRATION | RELYING_PARTY_SERVER | Listing request for mobile devices or security keys registered to the user. |
| OOB_WEBSITE_REG | REGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER MobileDevice WEB | The opening registration request from the browser or workstation. The client now waits for the mobile to scan QR. Started. |
| OOB_WEBSITE_REG | REGISTRATION | RELYING_PARTY_SERVER MobileDevice WEB | The client setup is complete. The sessionId is returned to the client This indicates that the device has finished enrolling the user key pair. Registration is not yet complete. |
| OOB_WEBSITE_REG | REGISTRATION MOBILE_DEVICE | RELYING_PARTY_SERVER MobileDevice WEB | The opening registration request call from the browser or workstation. The client now waits for the mobile device to scan a QR code. Typical problems: - The Application is not setup in Control Center - The HYPR license is invalid |
| OOB_WORKSTATION_REG | REGISTRATION | RELYING_PARTY_SERVER MobileDevice Workstation | FIDO registration was started. |
| SMARTKEY_ENROLL | REGISTRATION WORKSTATION | RELYING_PARTY_SERVER Workstation | Enrolling the security key. enrollmentRequest=[req] |
| SMARTKEY_ENROLL_COMPLETE | REGISTRATION | RELYING_PARTY_SERVER | Security key enrollment succeeded. |
RISK_ENGINE Events
Event (eventName) | Action | Source (eventLoggedBy) | Description ( message) |
|---|---|---|---|
| ADAPT_CREATE_POLICY | ADAPT AUTHENTICATION | CONTROL_CENTER_SERVER | Created new Adapt authentication policy for this tenant. |
| ADAPT_DELETE_POLICY | ADAPT ADMIN RISK_ENGINE (AUTHENTICATION) | CONTROL_CENTER_SERVER | Deleted an Adapt authentication policy for this tenant. |
| ADAPT_LOGGING_ONLY_POLICY_EVALUATION | ADAPT AUTHENTICATION | CONTROL_CENTER_SERVER | Adapt policy evaluation was successful for evaluationPoint=, policyName=, policyId=, message= |
| ADAPT_POLICY_ASSIGNMENT | ADAPT ADMIN RISK_ENGINE | CONTROL_CENTER_SERVER | Updated Adapt policy assignment for evaluationPoint=* to policyId= with adaptUnavailableFallback=[STANDARD | QR_ONLY | BLOCKED]. |
| ADAPT_POLICY_ASSIGNMENT_REMOVED | ADAPT ADMIN RISK_ENGINE | CONTROL_CENTER_SERVER | Removing Adapt policy assignment for evaluationPoint=. |
| ADAPT_POLICY_ASSIST | ADAPT ADMIN RISK_ENGINE | CONTROL_CENTER_SERVER | Request for policy assistance was made for policyId=[policyId], policyName=[policyName]. |
| ADAPT_POLICY_EVALUATION | ADAPT AUTHENTICATION | CONTROL_CENTER_SERVER | Adapt policy evaluation was successful for , rpAppId=, traceId=<traceId, if applicable; may be empty>. |
| ADAPT_POLICY_EVAL_USER_ALLOWLISTED | ADAPT ADMIN RISK_ENGINE | CONTROL_CENTER_SERVER | User=, rpAppId=[rpAppId] has been allowlisted from Policy Evaluation by adminUser= |
| ADAPT_POLICY_EVAL_USER_BLOCKED | ADAPT ADMIN RISK_ENGINE | CONTROL_CENTER_SERVER | The limit for allowed login failures was exceeded. OR Accompanies a 403 status code. |
| ADAPT_POLICY_UNASSIGN_DELETED_POLICY | ADAPT ADMIN RISK_ENGINE | CONTROL_CENTER_SERVER | Removed Adapt policy assignments evaluationPoints= to policyId= because the policy has been deleted. |
| ADAPT_UPDATE_POLICY | ADAPT ADMIN RISK_ENGINE | CONTROL_CENTER_SERVER | Update an Adapt authentication policy for this tenant. |
SETTINGS Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| SSL_PINS_UPDATED | ADMIN MOBILE_DEVICE WORKSTATION | MobileDevice Workstation | SSL pins have been synched across HYPR. [Fail] Error updating SSL pins: Operation failed |
| UPDATE_SERVER_GLOBAL_CONFIG | ADMIN | RELYING_PARTY_SERVER | Support email has been updated. Support display name has been updated. OR Support email has been deleted. |
| FIDO2_POLICY | SETTINGS | RELYING_PARTY_SERVER | Updated FIDO2 policy. |
| FIDO2_SETTINGS | SETTINGS | RELYING_PARTY_SERVER | [Client origin URL] has been [ enabled | disabled ] |
SIGNAL Events
Event (eventName) | Action | Source (eventLoggedBy) | Description ( message) |
|---|---|---|---|
| DEVICE_SIGNAL_RECEIVED | SIGNAL | RELYING PARTY_SERVER | Successfully posted the device security state. |
| WORKSTATION_SIGNAL_RECEIVED | SIGNAL | RELYING_PARTY_SERVER | Successfully posted the workstation security state. |
| BROWSER_SIGNAL_RECEIVED | SIGNAL | BROWSER | Successfully posted the browser security state. |
SMART_KEY Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| SMARTKEY_CC_INITIATED_UNENROLL | SMART_KEY WORKSTATION | RELYING_PARTY_SERVER | The security key was unenrolled from Control Center. Please remove the certificate from the Certificate Authority using the following command: certutil -revoke ${req.smartKeyCertificateSerialNumber} 8 |
| SMARTKEY_PIN_CHANGE | SMART_KEY WORKSTATION | Workstation | An attempt was made to change the security key PIN. |
| SMARTKEY_PIN_VERIFICATION | SMART_KEY WORKSTATION | Workstation | The security key PIN was verified. |
| SMARTKEY_WORKSTATION_INITIATED_UNENROLL | SMART_KEY WORKSTATION | RELYING_PARTY_SERVER Workstation | The security key was unenrolled from the workstation. Please remove the certificate from the Certificate Authority using the following command: certutil -revoke ${req.smartKeyCertificateSerialNumber} 8 |
| SMARTKEY_AUTH | SMART_KEY WORKSTATION | [Not Logged] | Authentication was attempted on a workstation using a security key. |
| SMARTKEY_AUTH_COMPLETE | SMART_KEY WORKSTATION | Workstation | Authentication was completed using a security key. |
| SMARTKEY_PIN_PUK_CHANGE | SMART_KEY WORKSTATION | [Not Logged] | A PIN Unblocking Key (PUK) for a smart key has been changed. |
| SMARTKEY_PIN_PUK_VERIFICATION | SMART_KEY WORKSTATION | [Not Logged] | A PIN Unblocking Key (PUK) for a smart key has been verified as part of a PIN reset. |
| SMARTKEY_RECOVERY_PINS_RE_GENERATED | ADMIN RECOVERY_PINS SMART_KEY | [Not Logged] | Recovery pins re-saved. |
| SECURITY_KEY_PUK_READ | SMART_KEY | When the cc/api/securitykey/getpinreset endpoint is called. | |
| SECURITY_KEY_PUK_UPDATE | SMART_KEY | When the cc/api/securitykey/updaterecovery endpoint is called with a Workstation Installation token. This event is generated whether the update is successful or not, and will contain the old and new values. | |
| SECURITY_KEY_PUK_CREATE | SMART_KEY | A new PUK record has been created. |
SUPPORT_ACCESS Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| SUPPORT_ACCESS_ENABLED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | HYPR Support access enabled. |
| SUPPORT_ACCESS_DISABLED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | HYPR Support access disabled. |
| SUPPORT_ACCESS_EXPIRATION_DATE_CHANGED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | HYPR Support access expiration date set. |
| SUPPORT_ACCESS_EXPIRATION_DATE_EXCEEDED_BLOCKING_ACCESS | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Blocked HYPR Support access due to expiration date exceeded. |
| SUPPORT_ACCESS_NEW_EXPIRATION_DATE_APPLICABLE_ENABLING_ACCESS | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Enabled HYPR Support access due to expiration date no yet exceeded. |
| SUPPORT_ACCESS_ADDED_EMAILS_TO_ALLOW_LIST | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Email added to list. |
| SUPPORT_ACCESS_REMOVED_EMAILS_FROM_ALLOW_LIST | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Email removed from list. |
| SUPPORT_ACCESS_ALLOWANCE_CHANGED_FROM_ALLOW_LIST_TO_ALL | SUPPORT_ACCESS | RELYING_PARTY_SERVER | All HYPR employees are allowed to have access. |
| SUPPORT_ACCESS_ALLOWANCE_CHANGED_FROM_ALL_TO_ALLOW_LIST | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Only HYPR employees on the list are allowed to have access. |
| SUPPORT_ACCESS_EXPIRATION_DATE_ENABLED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Changed from indefinite access to expiration date. |
| SUPPORT_ACCESS_EXPIRATION_DATE_DISABLED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Changed from expiration date to indefinite access. |
| SUPPORT_ACCESS_DENIED_TENANT_ACCESS_ATTEMPT_EXPIRATION_DATE_EXCEEDED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Denied HYPR Support access - expiration date exceeded. |
| SUPPORT_ACCESS_SUCCESSFUL_TENANT_ACCESS_ATTEMPT | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Successful HYPR Support tenant access. |
| SUPPORT_ACCESS_DENIED_TENANT_ACCESS_ATTEMPT_UNAUTHORIZED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Denied HYPR Support access - unauthorized. |
| SUPPORT_ACCESS_DENIED_TENANT_ACCESS_ATTEMPT_SUPPORT_ACCESS_DISABLED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | Denied HYPR Support access - access disabled. |
| SUPPORT_ACCESS_MAGIC_LINK_SESSION_EXPIRED | SUPPORT_ACCESS | RELYING_PARTY_SERVER | HYPR Support Magic Link session expired. |
SYSTEM_CHECK Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| BATCH_DB_UPDATE | SYSTEM_CHECK | CONTROL_CENTER_SERVER | The background process to update the database failed; contact your administrator immediately. |
| DB_CRYPTO_VALIDATION_PROBLEM | SYSTEM_CHECK | CONTROL_CENTER_SERVER | The database data integrtity check failed. Data has potentially been tampered with. Check affected user activity in the Audit Trail and Logs for suspicious authentication attempts. Try to register again. |
| FIDO_CERT_EXPIRY_CHECK | SYSTEM_CHECK | RELYING_PARTY_SERVER | Certificate Expiration Notice. FIDO certificates are monitored for expiry based on days remaining: < 90 = High Criticality 90 - 150 = Medium Criticality > 150 = Low Criticality If the event is not logged as success=false, it passed the check. |
| LICENSE_VALIDATION_PROBLEM | SYSTEM_CHECK | RELYING_PARTY_SERVER | INVALID_LICENSE: Details: Please upload a HYPR license key with a valid domain. Creating and updating RP applications will not be permitted until a valid license is uploaded. |
| MOBILE_CERT_RENEWAL_EXPIRY_CHECK | SYSTEM_CHECK MOBILE_DEVICE | RELYING_PARTY_SERVER MobileDevice | Certificate Expiration Notice. Mobile device certificates are monitored for expiry based on days remaining: < 90 = High Criticality 90 - 150 = Medium Criticality > 150 = Low Criticality If the event is not logged as success=false, it passed the check. |
| UAF_CERT_EXPIRY_CHECK | SYSTEM_CHECK | RELYING_PARTY_SERVER | Certificate Expiration Notice. UAF certificates are monitored for expiry based on days remaining: < 90 = High Criticality 90 - 150 = Medium Criticality > 150 = Low Criticality If the event is not logged as success=false, it passed the check. |
WEB_REGISTRATION Events
Event (eventName) | Action | Source (eventLoggedBy) | Description (message) |
|---|---|---|---|
| MOBILE_CANCELLED_NEW_CERTIFICATE | WEB_REGISTRATION | RELYING_PARTY_SERVER | Mobile cancelled workstation certificate processing. |
| MOBILE_CONFIRMED_CERTIFICATE_RENEWAL | WEB_REGISTRATION | [Not Logged] | The mobile device's certificate renewal is complete. |
| MOBILE_CONFIRMED_NEW_CERTIFICATE | WEB_REGISTRATION | RELYING_PARTY_SERVER | The mobile device confirms workstation certificate processing. |
| MOBILE_NOTIFIED_OF_CERTIFICATE_RENEWAL | WEB_REGISTRATION | [Not Logged] | The mobile device was informed of successful certificate renewal. |
| MOBILE_NOTIFIED_OF_NEW_CERTIFICATE | WEB_REGISTRATION | RELYING_PARTY_SERVER | The mobile device has been notified of the workstation certificate's availability. |
| WORKSTATION_CERTIFICATE_ISSUED | WEB_REGISTRATION | RELYING_PARTY_SERVER | The certificate was issued by the enrollment service. |
| WORKSTATION_CERTIFICATE_REQUESTED | WEB_REGISTRATION | RELYING_PARTY_SERVER | A certificate request has been queued up for the Enrollment service. |
| WORKSTATION_CERTIFICATE_REVOKED | WEB_REGISTRATION | [Not Logged] | The workstation certificate was revoked. |
| WORKSTATION_ENROLLED | WEB_REGISTRATION | RELYING_PARTY_SERVER | Workstation enrolled. [machineName] |
WORKSTATION and WORKSTATION_STATE Events
Event (eventName) | Action | Source (eventLoggedBy) | Description ( message) |
|---|---|---|---|
| WORKSTATION_CONFIGURATION | WORKSTATION_STATE WORKSTATION | [Not Logged] | The workstation was configured successfully. |
| WORKSTATION_INSTALL_TOKEN | WORKSTATION_STATE WORKSTATION | Workstation | Failed to exchange install token. Exception during install exchange. |
| WORKSTATION_LOCK | WORKSTATION_STATE MOBILE_DEVICE | RELYING_PARTY_SERVER Workstation | A request was issued to lock the workstation. [deviceId(deviceIdParam)] |
| WORKSTATION_SOCKET_CONNECT | WORKSTATION_STATE WORKSTATION | Workstation | The workstation web socket was connected. |
| WORKSTATION_SOCKET_DISCONNECT | WORKSTATION_STATE | [Not Logged] | The workstation web socket was disconnected. |
| WORKSTATION_SHUTDOWN | WORKSTATION_STATE WORKSTATION | [Not Logged] | The workstation was shut down. Usually this indicates the user powered off or rebooted the computer. |
| WORKSTATION_STARTUP | WORKSTATION_STATE WORKSTATION | [Not Logged] | The workstation was started. Usually this indicates the user powered on or rebooted the computer. |
| WORKSTATION_UPGRADE | WORKSTATION_STATE WORKSTATION | [Not Logged] | The workstation was upgraded. |
Event Parameters
Each Event will provide the following parameters, data permitting.
Labels in plain text are directly from the Event Data Model, while those in italics are generated for the logs and may be used in the Audit Trail and HYPR Dashboard for Splunk.
| Parameter | Description |
|---|---|
additionalDetails | A map of discretionary data supplied for an Event; used to capture attributes not available in the Event object. |
authenticator | Authenticator GUID/ID logged with the following Events: GUID for FIDO2 Authentication FIDO2_DEVICE_DEREG FIDO2_WEBAUTHN_COMPLETE FIDO2_DEVICE_REG_COMPLETE ID for UAF FIDO_ONLY_AUTH FIDO_ONLY_DEREG FIDO_ONLY_REG Authenticator Type for the following Events: Biometric or PIN for Security Key Desktop Authentication SMARTKEY_AUTH_COMPLETE |
errorCode | The HYPR Error code associated with the Event, if any. This value must be populated if isSuccessful=false. See also HYPR Error Codes Troubleshooting Tables. |
errorSeverity | The impact level of the Event causing the error. Possible Values: WARN, ERROR, FATAL, null (default) |
eventLoggedBy | The component which logged the Event. Success Events are mostly (but not necessarily) logged by the server. Failure Events are sent by the HYPR Mobile App, HYPR Passwordless, or HYPR SDK if something goes wrong. Possible Values: MobileDevice, RELYING_PARTY_SERVER, CONTROL_CENTER_SERVER, Web, Workstation, Browser, UAF_SERVICE, ENROLLMENT_SERVICE |
eventName | The name of the Event. |
eventTimeInUTC | The time of the Event in UTC format. |
fidoUser | A machine-readable user handle representing a FIDO registration. |
id | Unique identifier for the Event. |
integrationProvider | The type of integration provider for the Event, based on the rpAppId.AZURE_AD, BEYOND_TRUST, FORGE_ROCK, GOOGLE, OKTA, ONELOGIN, OPENID_CONNECT, PING_DAVINCI, PING_ID, RADIUS |
integrationType | The type of integration upon which the Event occurs. Possible values: IDP, EAM, FIDO2 |
isSuccessful | Status of the individual Event. Possible values: true, false |
loggedTimeInUTC | The time the server logged the Event in UTC format. |
machineUserName | HYPR name for the user generating the Event. Typically associated with fidoUser. |
message | A message giving a brief recount of the Event. |
remoteIP | The IP address of the node submitting the Event. Sourced from the X-Forwarded-For HTTP header in the request. |
rpAppId | The camel case unique identifier of the relying party application generating the Event. |
sessionId | Unique identifier of the web session. |
version | The Event schema version. |
subName | An Event might be broken into sub-steps. The SubEvent distinguishes the various steps. Typically it is the URI of the request. |
tenantId | Identifier for the HYPR Control Center server. Sourced from the HYPR-TenantID HTTP header or from the hypr.rp.cacheNamespace Vault prop. |
tokenType | The type of token being passed. - BEARER: API Authorization token used by Postman. - OAUTH_CLIENT_CREDENTIALS: OAuth credentials created in Control Center. - OAUTH_CLIENT_CREDENTIALS_ACCESS_TOKEN: An OAuth access token, used the same way as a Bearer token to access the HYPR Passwordless API. |
traceId | An identifier to assist Support in tracking the Event. If the header is missing, the server starts a new trace. Sourced from the X-B3-TraceId HTTP header. |
type | Event classification. For API log requests, this will always be AUDIT. |
usageType | Currently not used. |
userAgent | Identifies the application, operating system, vendor, and/or version of the Event's requesting user agent. Sourced from the User-Agent HTTP header. |
Specific Parameters
The following parameters will appear only when a specific Event type is triggered.
Device (Includes Security Keys)
| Parameter | Description |
|---|---|
deviceId | A HYPR-generated device identifier. deviceId stays same for the lifetime of the App. Reinstalling the App generates a new deviceId. In this case, Device may refer to a mobile device (90%) or another hardware device (YubiKey, etc.) which stores the private key/authenticator and performs authentication. |
deviceModel | Device model number. Sourced from the HYPR-Device-Model HTTP header. |
deviceOS | Device operating system (Android/iOS/security key). Sourced from the HYPR-Device-OS HTTP header. |
deviceOSVersion | Device operating system version. For security keys, this will be the firmware version. Sourced from the HYPR-Device-OS-Version HTTP header. |
deviceRelVersion | Version of the HYPR Mobile App. Sourced from the HYPR-Device-Release-Version HTTP header. |
deviceType | Represents any special indication of the device type triggering the Event. [ MOBILE | SECURITY_KEY | WEBAUTHN ] |
sdkRelVersion | Version of the HYPR SDK. Sourced from the HYPR-SDK-Release-Version HTTP header. |
tokensAvailable | Number of Offline Mode tokens available. |
tokensRemaining | Number of Offline Mode tokens remaining. |
Workstation
| Parameter | Description |
|---|---|
extendedMessage | An additional message from the workstation regarding the Event. |
machineId | A HYPR-generated machine identifier. In this case, Machine refers to the entity requesting authentication. Possible Values: Website Accessing the same website in different browsers is considered to be the same machine. machineId is derived as sha256(window.location.hostname + user + rpAppID) WorkStation The UUID generated upon Workstation install. This is not related to the underlying OS. The machineId remains constant through the life of the install or upgrade. A re-install of the Workstation will generate a new machineId." |
machineType | Defines when a machine is persisted/non-persisted with a local, web, or domain account. Possible values: - WEB: Persisted workstation with local account website- WORKSTATION: Persisted workstation with local account- WORKSTATION_DOMAIN: Persisted workstation with domain account- VDI: Non-persisted workstation with non-domain account |
offlineAccessDays | Number of days remaining on offline tokens. |
offlineAccessEnabled | Toggle Offline Access. Possible Values: True, False |
offlineTokenCount | Total number of offline tokens. |
offlineTokenLength | Length of the offline token. |
tokensAvailable | Number of tokens available. |
tokensRemaining | Number of tokens remaining. |
wsModel | Workstation model number. Sourced from the HYPR-WS-Model HTTP header. |
wsOS | Workstation operating system. Sourced from the HYPR-WS-OS HTTP header. |
wsOSVersion | Workstation operating system version. Sourced from the HYPR-Device-OS-Version HTTP header. |
wsRelVersion | Version of the HYPR Passwordless client. Sourced from the HYPR-WS-Release-Version HTTP header. |
Server
| Parameter | Description |
|---|---|
node | IP address of the node. |
serverRelVersion | Version of the HYPR Control Center. |
Web
| Parameter | Description |
|---|---|
extendedMessage | Additional details. |
machineName | Unique name of the machine. |
Identity Verification - HYPR Affirm
| Parameter | Sub-parameter | Description |
|---|---|---|
affirmResult | Boolean value indicating approval or denial. [ true | false ] | |
affirmResultType | Choose the behavior after identity verification is complete: - MAGIC_LINK: The user will be routed to the Control Center Device Manager via a Magic Link - TAP: Entra ID users will be given a temporary access pass - None: Used when affirmation fails or the approver denies verification. | |
affirmVerificationFlow | An object containing the configuration data for the Verification Flow as the tab of the same name in Control Center. | |
affirmVerificationFlow.approverAttestationRequired | Boolean value indicating whether or not the approver attestation is required. Enabled by default. [ true | false ] | |
affirmVerificationFlow.chatApproverRequired | Boolean value indicating whether or not the chat is required. [ true | false ] | |
affirmVerificationFlow.chatCheck | Boolean value indicating whether or not basic chat is enabled. [ true | false ] | |
affirmVerificationFlow.chatDocumentRequired | Boolean value indicating whether or not document upload is required in chat. [ true | false ] | |
affirmVerificationFlow.chatSelfieEnabled | Boolean value indicating whether or not the chat selfie feature is enabled. [ true | false ] | |
affirmVerificationFlow.chatSelfieRequired | Boolean value indicating whether or not the selfie requirement is enabled. [ true | false ] | |
affirmVerificationFlow.idvCheck | Boolean value indicating whether or not the identity verification checks category is enabled. [ true | false ] | |
affirmVerificationFlow.idvNameCheck | Boolean value indicating whether or not the name checks are enabled. [ true | false ] | |
affirmVerificationFlow.locationCheck | Boolean value indicating whether or not the location checks are enabled. [ true | false ] | |
affirmVerificationFlow.phoneNumberCheck | Boolean value indicating whether or not the Phone Number checks are enabled. Enabled by default. [ true | false ] | |
affirmVerificationFlow.smsCheck | Boolean value indicating whether or not the SMS checks are enabled. If phoneNumberCheck is true, this will also be true. [ true | false ] | |
affirmVerificationFlow.videoChatCheck | Boolean value indicating whether or not video chat image capture comparison is enabled. [ true | false ] | |
approver | The name of the approver. | |
approverEmail | The approver's email address. | |
attestationComment | A free text field to hold approver comments. | |
attestationResult | Boolean value indicating the success of attestation. [ true | false ] | |
attestationTimestamp | The Epoch timestamp of the attestation. | |
conversationId | Unique identifier for the conversation. | |
costsTracking | The data object used to track costs. | |
costsTracking.exceptionMessage | Displays additional error codes if applicable. | |
costsTracking.incursCost | Boolean value to confirm cost-incurring requests. [ true | false ] | |
costsTracking.isSuccessful | Boolean value indicating success or failure. [ true | false ] | |
costsTracking.messages | A list of messages in the verification flow. | |
costsTracking.operation | Varies depending on costsTrackingPlatform: GOOGLE_LOCATION: - GOOGLE_LOCATION_DISTANCE - GOOGLE_LOCATION_ADDRESS AWS_PINPOINT: - AWS_PINTPOINT_INVITE_SEND_EMAIL - AWS_PINTPOINT_INVITE_SEND_TEXT - AWS_PINPOINT_SMS_SEND AWS_REKOGNITION: - AWS_REKOGNITION_FACE_MATCH_IN_PROGRESS - AWS_REKOGNITION_FACE_MATCH_RESULT TWILIO: - TWILIO_VIDEO_ACCESS_TOKEN_CREATED - TWILIO_PHONE_NUMBER_V1 - TWILIO_LOOKUP_CARRIER_DATA - TWILIO_NEW_CONVERSATION - TWILIO_EXISTING_CONVERSATION | |
costsTracking.participants | A list of participants in the verification flow. | |
costsTracking.platform | The platform used for cost tracking. [ GOOGLE_LOCATION, AWS_PINPOINT, AWS_REKOGNITION, TWILIO, NONE ] | |
faceMatchResult | Indicates the state of the facial recognition matching. If this feature is not enabled, this value will be null. [ null | MATCH | IN PROGRESS ] | |
flow | Is this for Onboarding or Recovery? [ ONBOARDING | RECOVERY ] | |
inviteEmail | Email address used if inviteSendVia is set to EMAIL. | |
inviteSendVia | Method by which the invitation is sent. [ EMAIL | SMS ] | |
locationIpDistance | Location data derived from the requester's browser and IP address data. Expressed as '[distance] from home address'. | |
locationReverseGeocodeDistance | Distance expressed as a number of units. | |
phoneNumberVerified | Boolean value indicating whether or not the phone number has been verified. [ true | false ] | |
state | The state of the Application Association. [ ENABLE | DISABLE | REMOVE ] | |
textCodeSent | Boolean value indicating whether or not an SMS code has been sent. [ true | false ] | |
textCodeVerified | Boolean value indicating whether or not an SMS code has been verified. [ true | false ] | |
userRole | What role is this user? Requester | Approver | |
video | Boolean value that determines whether or not a video chat will connect the requester and approver. [ true | false ] | |
videoChatRoomName | The label for the video chat room. | |
workflowId | Unique identifier for the Affirm workflow. |
Event Log File (On-premises Only)
HYPR generates Event log files for tracing errors and Events, and to help integration with SIEM tools such as Splunk, Greylog, etc.
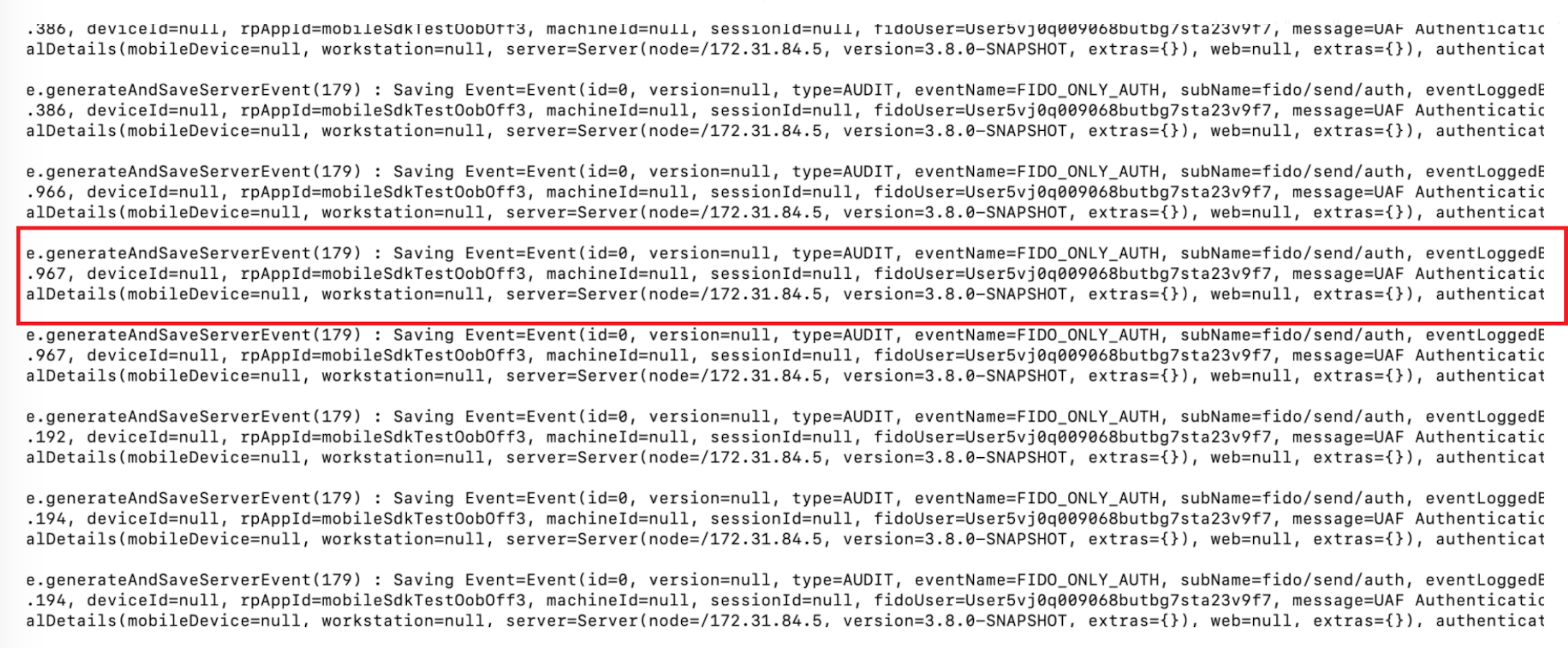
Control Center Event Log File
The CC Event log is located under the /opt/hypr/<server install dir> logs directory. It contains all Control Center Events.
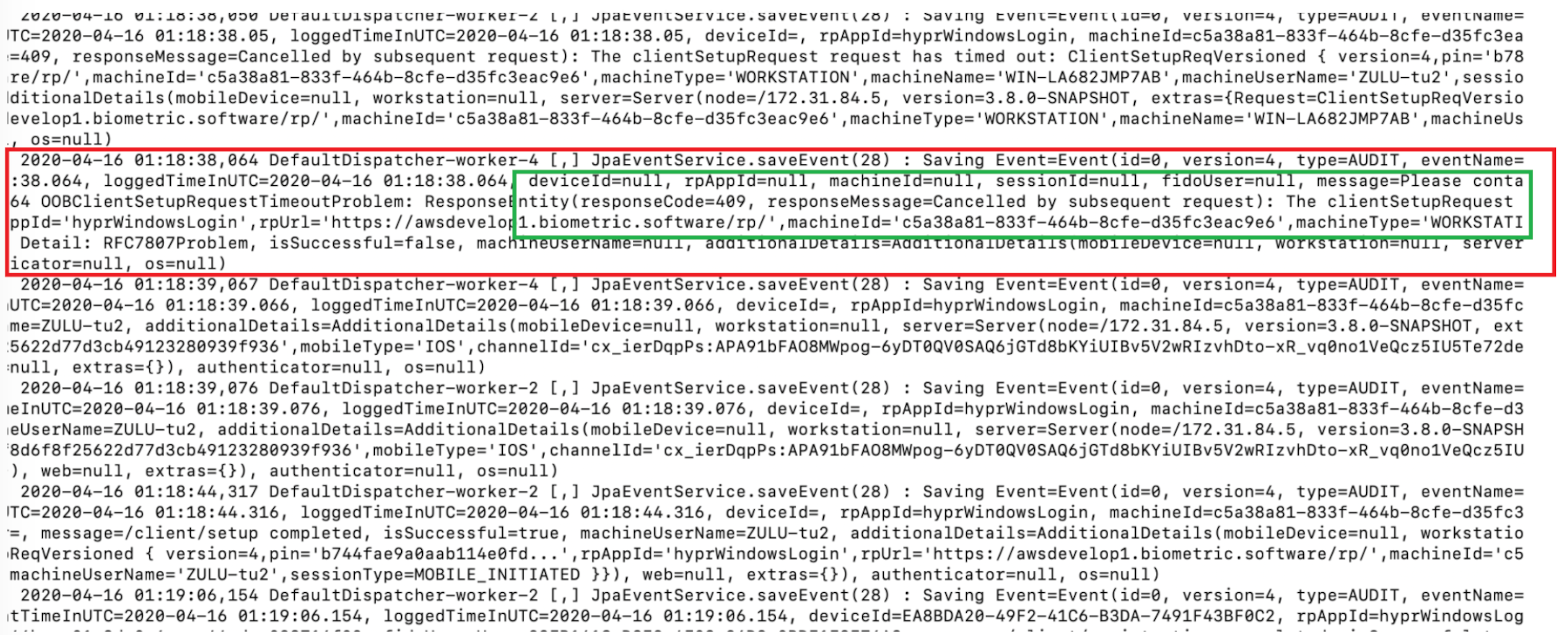
UAF Event Log File
The UAF Event log is located in the /opt/hypr/<server install dir> logs directory. This contains all UAF Events.