(Windows) Unlock Fails after Expired Certificate
Two methods can be used to diagnose whether or not a Windows unlock attempt via HYPR Passwordless client has failed due to an expired certificate.
Obtain the KSP Logs
-
Open regedit on the affected workstation.
-
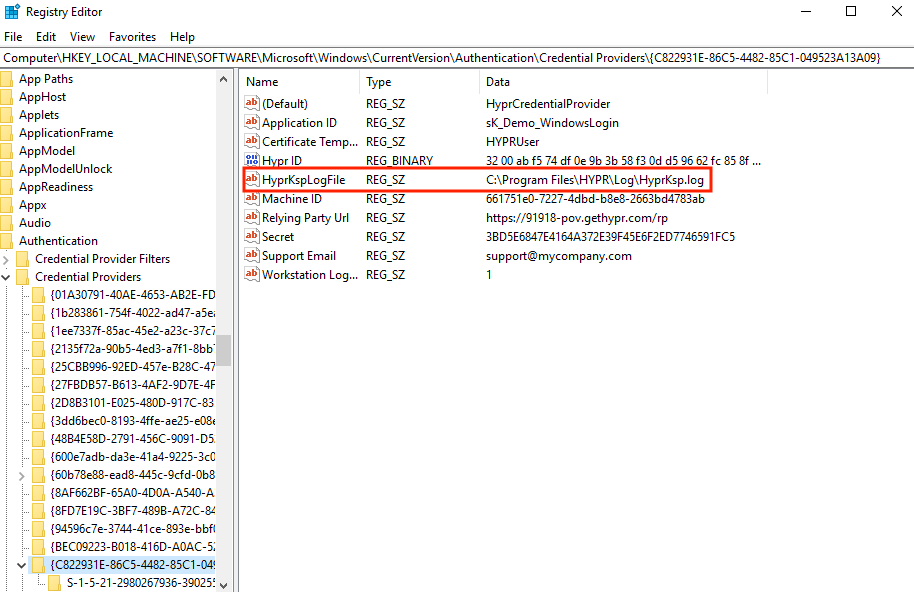
Navigate to HYPR registry record:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{C822931E-86C5-4482-85C1-049523A13A09}. -
Create a new registry Key (String/Value) called
HyprKspLogFileand provide a path to the file, e.g.,C:\Program Files\HYPR\Log\HyprKsp.log.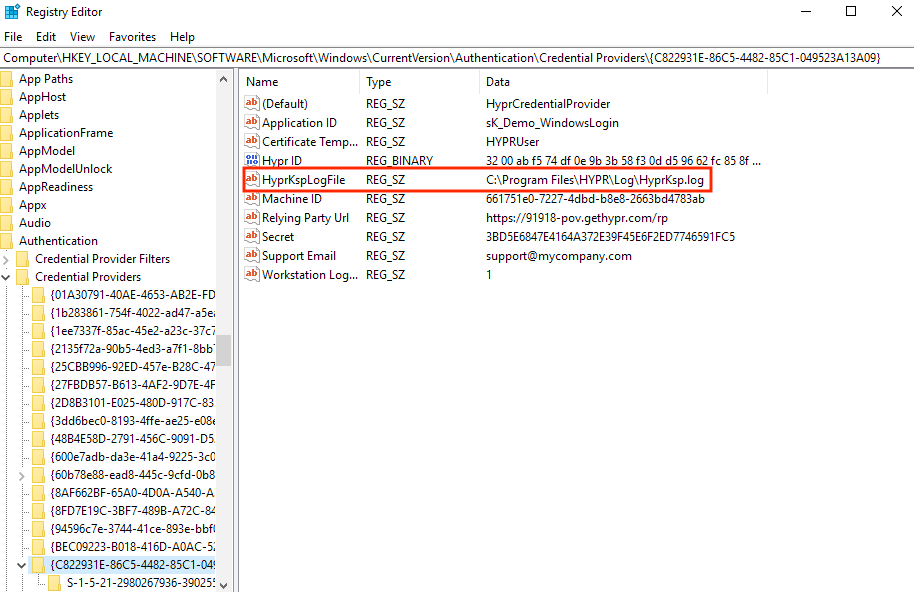
-
Restart the HYPR Windows service or reboot to enable the changes.
-
The log file will show the total time for certificate revocation checks and account checks (disabled/deleted). Search for revocation and you'll find where it's doing the checks.
-
Look for
KSPCertUtils_IsCertificateExpired, indicating the certificate has expired -
If it’s there with a recent timestamp, the affected user(s) will need to re-enroll
-
Unlock Failed Due to Expired Cert
-
Run the following command substituting the path value to the KSP log file, as shown in Step 2, above:
certutil -v -template **<value in the Certificate Template in Regedit>**
-
In the results, look for the following and determine the certificate's expiration:
diagnosePwcUnlockFailureDueToExpiredCertWindows_1.png -
To look for additional certificates, run the following command and look for any certificates that start with HYPR:
certutil -v -template -
Call the above code.
certutil -v -template <HYPR Cert from calling certutil -v -template>