Intune Adapt Policy Setup
This article is subject to change as the feature develops and we make improvements.
The calls to perform CRUD operations and to test HYPR Adapt Risk Policies, including the allowlisting of users, can be found here in the HYPR Passwordless API collection.
This documentation will give you a clear understanding on how to set up the Intune Adapt policy and how it works. The Intune Adapt policy is currently set up in two parts: The policy itself, and the signal handler. Both of them are available in the HYPR Control Center. For HYPR control center to communicate with Entra, an App Registration must be configured with the correct permissions.
Entra Configuration
With a HYPR Entra Integration
When configuring Entra with HYPR you are required to create an App Registration (see the Instructions here). Within the HYPRAuthApp, add the following API permission as an application type (DeviceManagementManagedDevices.Read.All). Make sure after you add the permissions to click on, “Grant admin consent for”.
Without a HYPR Entra Integration
If you are not using the Entra integration with HYPR, you must create a new App Registration and add the correct permissions.
-
Open Entra ID and click on App Registrations on the left side.
-
Click on New Registration.
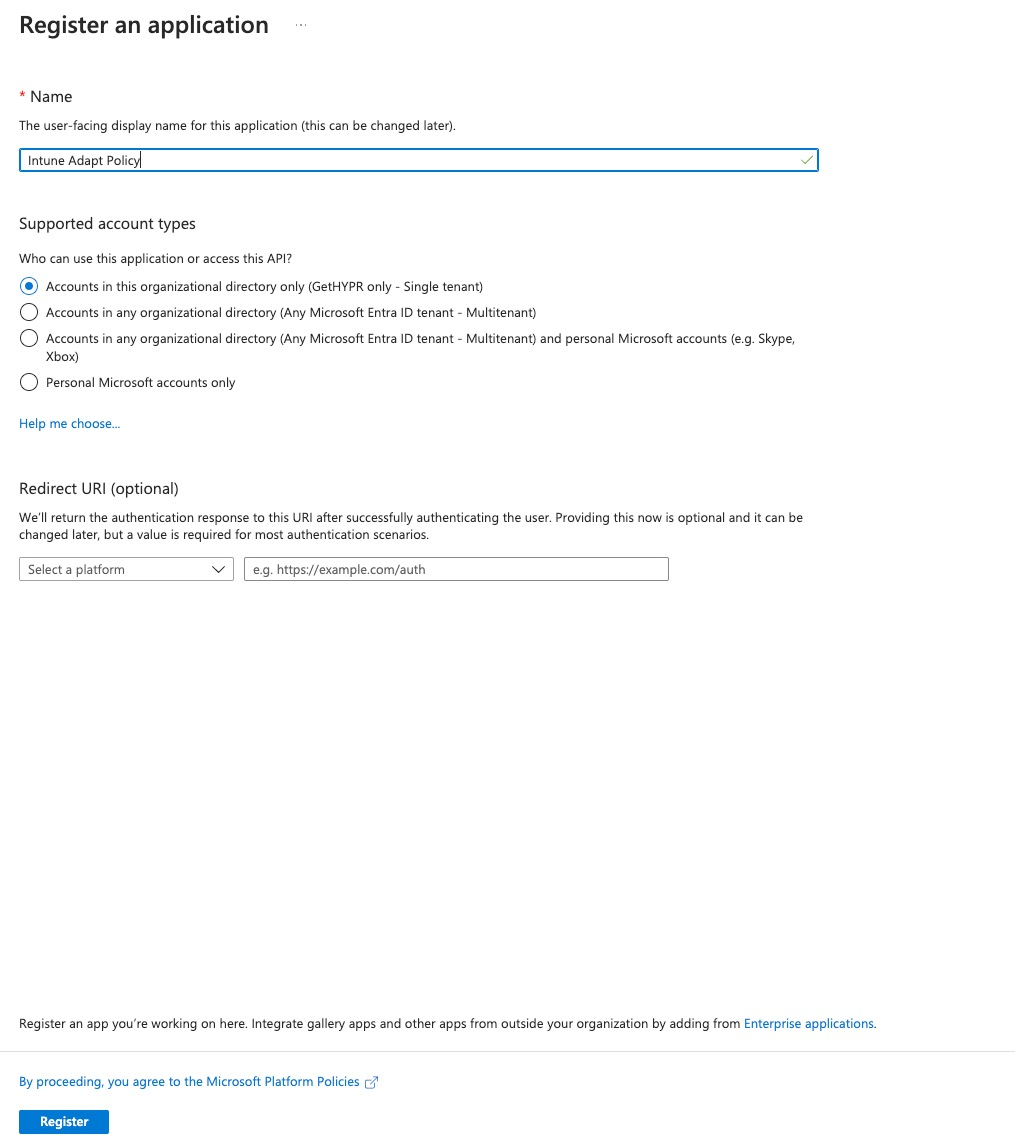
-
Name it 'Intune Adapt Policy'.
-
You will see the new App Registration. Click on API Permissions at left.
-
Click Add a Permission, then select Microsoft Graph and Application permissions.
-
Look for DeviceManagementManagedDevices.Read.All. Select the permission.
-
Click Add Permissions.
-
Once the permissions have been added, select Grant admin consent for.
HYPR Adapt Policy Config: Risk Policies
Prerequisites
-
Contact HYPR Support to enable the Adapt Policies feature.
-
Obtain the latest version of the Intune Adapt Policy from HYPR
Configure the Intune Policy in Control Center
We will now configure the Intune Adapt policy within HYPR Control Center.
-
Log in to the HYPR Control Center as an Admin.
-
Click +Risk Policy.
-
Select Workstation Unlock, then Custom.
-
Name the policy Intune Policy.
-
Once created, click the policy and select Configuration.
-
Select the Test tab and paste the policy code into the form. It will look similar to the following example.
package authz
import future.keywords
import future.keywords.if
# Converted system time from nanoseconds to milliseconds for proper comparison
currentSystemTime := time.now_ns()/1000000
# Required
default allowed := false
default allowedAuthenticators = []
default message = "OK"
#######################################
# Get WFA serial number from signal
#######################################
latestWFASignalSerialNumber = result {
filtered_events := [e |
e := input.events[_]
e.eventName == "WORKSTATION_SIGNAL_RECEIVED"
e.isSuccessful == true
]
# Extract event times from the filtered events
event_times := [e.eventTimeInUTC | e := filtered_events[_]]
sorted_times := sort(event_times)
# Get the last event time
last_time := sorted_times[count(sorted_times) - 1]
# Find the event with the last event time
event := filtered_events[_]
event.eventTimeInUTC == last_time
serialNumber := event.additionalDetails.workstationSignal.system.biosSerialNumber
result = removeSpaces(serialNumber)
}
#######################################
# Get latest Intune Compliance event for machine
#######################################
latestMachineIntuneEvent = result {
machineEvents := getMachineIntuneEvents
# Extract event times from the filtered events
event_times := [e.eventTimeInUTC | e := machineEvents[_]]
sorted_times := sort(event_times)
# Get the last event time
last_time := sorted_times[count(sorted_times) - 1]
# Find the event with the last event time
event := machineEvents[_]
event.eventTimeInUTC == last_time
result := event
}
#######################################
# HELPER FUNCTIONS
#######################################
# Function to check if a value exists and is not null
existsNotNull(value) = true {
value != null
} else = false {
value == null
}
removeSpaces(serialNumber) = output {
parts := split(serialNumber, " ")
output := concat("", parts)
}
# Boolean value that checks if either of two objects is not null or exists
serialNumberFound = true {
existsNotNull(latestWFASignalSerialNumber)
} else = false
# Boolean value that checks if either of two objects is not null or exists
complianceEventFound = true {
existsNotNull(latestMachineIntuneEvent)
} else = false
machineIsCompliant = {
latestMachineIntuneEvent
}
#######################################
# Allowed and Message Statements
#######################################
allowed if {
not serialNumberFound
}
allowed if {
not complianceEventFound
}
allowed if {
machineIsCompliant
}
message = "Machine is in compliance with Intune policy" if {
machineIsCompliant
}
message = "Machine is not in compliance with Intune policy" if {
not machineIsCompliant
serialNumberFound
complianceEventFound
}
message = "Could not find compliance event for machine serial number" if {
not machineIsCompliant
serialNumberFound
not complianceEventFound
}
message = "No serial number found from user WFA signals. No compliance result can be checked" if {
not serialNumberFound
not machineIsCompliant
}
#######################################
# Query Local Dynamo Events for machines serial number
#######################################
current_time_millis := time_millis {
nanos := time.now_ns()
time_millis := nanos / 1000000
}
# Function to get the time one day ago in milliseconds
one_day_ago_millis := time_millis {
nanos := time.now_ns()
one_day_nanos := 24 * 60 * 60 * 1000000000
time_millis := (nanos - one_day_nanos) / 1000000
}
getMachineIntuneEvents = response {
serialNumber = latestWFASignalSerialNumber
# Define the input object structure
input_object := {
"securityToken": input.data.securityToken,
"entityIdOrName": serialNumber,
"startDate": one_day_ago_millis,
"endDate": current_time_millis
}
# Set up the HTTP request parameters
request := {
"method": "POST",
"url": "http://localhost:8182/local_search_events",
"headers": {
"Content-Type": "application/json"
},
"body": input_object
}
# Send the HTTP request and capture the response
response := http.send(request).body
}
http_send = response {
# Define the input object structure
input_object := {
"securityToken": input.data.securityToken,
"entityIdOrName": "NON_SENSE",
"startDate": one_day_ago_millis,
"endDate": current_time_millis
}
# Set up the HTTP request parameters
request := {
"method": "POST",
"url": "http://localhost:8182/local_search_events",
"headers": {
"Content-Type": "application/json"
},
"body": input_object
}
# Send the HTTP request and capture the response
response := http.send(request)
} -
Save the policy.
-
Select Policy Assignments.
-
Leave the configuration tab as is. Open the Test tab and conplete the fields as follows:
Application Select your workstation RP App Evaluation Point Workstation Pre-Unlock Evaluation Response Unavailable Fallback Standard Workflow -
Once you are finished, click Save.
-
In Policy Assignment, select +Policy Assignment.